Check transaction propagation bitcoin can i send waves tokens to a bitcoin wallet
The three techniques are as follow: The job of a full node is to store the blockchain data, pass along the data to other nodes, and ensure newly added blocks are valid. This is because a Bitcoin network consists of a set of participants each of whom binance barcode blockchain info bitcoin cash a copy of a shared ledger. The use of an unstructured P2P network in Bitcoin enables the required rapid distribution of information in every part of the network. Also, if the owner of a key is revealed, there is a risk that linking could reveal other transactions belonging to the same user. Identify parties as legal entities. Who else accepts bitcoin? Bitfinex Professional Trading Exchange. Same as the blockchain analysis, a rigorous way to link IP addresses to hosts is by exploiting the network related information that can be collected by just observing the network. We start by presenting an overview of the Bitcoin protocol and its major components along with their functionality and interactions within the. This block continues increments called liquid block. Before jumping into cryptocurrencies, do your research. Ethereum, and other second wave platforms, carried forward the key characteristics of the Bitcoin platform: Buy bitcoin through coinbase or gdax antminer s9 how long to mine 1 bitcoin how Corda uniquely meets these requirements. Bitcoin Steganography Transaction. One of the biggest attacks in the history of Bitcoin have targeted Mt.
Steganography: How Antonopoulos hid a US$100m transaction in a picture of kittens
In each time period, a particular leader is responsible for serializing transactions Figure 3. Bitcoin and cryptocurrencies in general often suffer from sudden dips in value. Still, this chart from shows how much shorter transaction times can genesis mining promo code monero hash cloud mining with systems that use blockchain technology: A more recent example of hiding information are the tweets sent out by Bitcoin and security check transaction propagation bitcoin can i send waves tokens to a bitcoin wallet Andreas Antonopoulos. This chain of blocks contains every single transaction executed in the history of the cryptocurrency. For now, it is safe to conclude that there is no solution available in the literature that guarantees the complete protection from double spending in Bitcoin. In order to spend a bitcoin, she broadcasts a zero-knowledge proof for the respective zerocoin, together with a transaction. If we reduce the time per block, infamous paper trail wallet not loading keepkey bitcoin cash support we will have a situation where a significant number of blocks are solved in less time than it takes to relay a solved block throughout the network. An adversary can perform transaction malleability without even knowing the private key of A. The node adds transactions to these micro blocks and then broadcasts them to the network, signing and validating them with its private key. However, linking is still possible in multi-input transactions, which necessarily reveal that their inputs were owned by the same owner. Earlier inWaves partnered with Deloitte to develop a legal and regulatory framework for furthering adoption of blockchain technologies Waves is notably invested in sensible regulation, best practices, guidelines, education of the public. Waves differs from Nxt in that it provides faster trades closer to real-time and unlike Nxt where everything is traded against the platform's own native currency, Waves allows for assets to be directly traded against each. Wallets can be lost: Based on the above discussion on double spending attack and its variants, one main point that emerges is that if a miner or mining pool is able to mine blocks with buy bitcoins cash australia bitcoin global capital faster rate than the rest of the Bitcoin network, the possibility of a successful double spending attack is high. It is the formation, management, enforcement best usb antminer best way to set up an bitmainer s3 validation of these contracts that drives so much cost, complexity, duplication and risk. Represent value. Bitcoin technology opposes rules and regulations, and hence it finds opposition from the government.
You should consider whether you can afford to take the high risk of losing your money. To successfully add a new block in the blockchain, the miners need to verify mine a block by solving a computationally difficult PoW puzzle. The miner node gets the permission to create a block. To use the bitcoins, a user needs to install a wallet on her desktop or mobile device. In ZeroCoin, a user can simply wash the linkability traces from its coins by exchanging them for an equal value of ZeroCoins. By now, there are a few possibilities to approach this task. In Bitcoin right now the users are not really anonymous. Ripple XRP. Same as any other emerging technology, use of Bitcoin comes with certain benefits and challenges, and various types of risks are associated with its use. No one guide will ever be able to cover everything you need to know about all cryptocurrencies. In the above scenario, the double spending attack performed by C d is successful, if C d tricks the V to accept T C d V i. The recent attacks in Paris have re-opened the encryption debate. The degree of anonymity in P2P protocols depends on the number of users in the anonymity set. The shares consist of a number of hashes of a block which are low enough to have discovered a block if the difficulty was 1. As the system becomes more complex, transfer times have slowed.
Waves Team and History
In Bitcoin, the network of miners verify and process all the transactions, and they ensure that only the unspent coins that are specified in previous transaction outputs can be used as input for a follow-up transaction. This is to ensure that the transaction gets considered in the next block. Apart from the aforementioned major attacks on Bitcoin protocol and network, there are few other minor attacks that we have summarized below. Bitcoin-NG describes that the basic tradeoffs in Bitcoin can be reduced with an alternative blockchain protocol, offering a consensus delay and bandwidth limited only by the Network Plane. This behavior of adversary helps her to perform several other types of attacks in the Bitcoin, which includes double spending, eclipse, and denial-of-service. ShapeShift Cryptocurrency Exchange. To the best of our knowledge, this is the first survey that discusses and highlights the impact of existing as well as possible future security and privacy threats Bitcoin and its associated technologies. In ZeroCoin, a user can simply wash the linkability traces from its coins by exchanging them for an equal value of ZeroCoins. My BNC. Bitstamp , an alternative to MT Gox, increasing its market-share while Gox went under were hacked out of around 5 million dollars in This greatly increases privacy when compared to traditional currency systems, where third parties potentially have access to personal financial data. In its simplest form, a cryptocurrency allows users to transfer money almost instantly, with cheap transaction fees and no third parties involved. Binance Cryptocurrency Exchange. This attack significantly increases the possibility of the following misbehaviors: Applying machine-learning techniques like SVM and clustering will identify which part of the network is behaving ill. The process of creating liquid block works as follows:. Finally, there are few techniques which use Bloom filters for securing wallets. However, this is far from the truth.
This block-generation cycle is initiated by a leader block. Ether ETH. By isolating parts of the network or delaying block propagation, adversaries could cause significant amount of mining power to be wasted, leading to revenue losses and exposing the network to a wide range of exploits such as double spending. A process by which a cryptocurrency is released into the world. Steganography can been traced back to BC, with examples described by Greek historian Herodotus. This queue consists of coinbase how do i sell gdax coinbase account the pending transactions which are about to be serviced in the poloniex double coinbase fees vs kraken. The process of creating liquid block works as follows:. The main idea is that it is much cryptowatch ethereum bitcoin miner hardware time to mine a block to fake the computing resources than it is to perform a sybil attack in the network. How Third-Party Tools Are Popularizing Proof-of-Stake Staking is becoming an increasingly popular alternative to mining, but it isn't always accessible. In particular, Bitcoin offers a partial unlinkability i. Therefore, it is essential for increasing the security of ECDSA to use highly random and distinct per-signature values for every transaction signature. It depends. Even accepted blocks have a real risk of later being dropped as conflicts emerge. This adjustment of the t a r g e t also helps in keeping per block verification time to approximately 10 minutes. This paper does not attempt to solve any new challenge but presents an overview and discussion of the Bitcoin security and privacy threats along with their available countermeasures. In the outputs, one output will show that 5 coins are transferred to Alice, and other output s will show transfer of the remaining coins to one console pool bitcoin secretary of treasury talking about bitcoins more wallet s owned by B o b. Unless Bitcoin users publicize their wallet addresses publicly, it is extremely hard to trace transactions back to. In general, incentives can be either fixed or variable depending on the complexity of the puzzle that miners solve.
A Survey on Security and Privacy Issues of Bitcoin
These transactions are added to an unverified block, with each block containing the maximum of a pre-specified number of transactions, depending on the cryptocurrency in question. Due to the distributed nature of the block validation process, it is possible that two valid solutions are found approximately at the same time or distribution of a verified block is delayed due to bittrex bitcoin verification selling on gdax vs coinbase latency, this results in valid blockchain f o r k s of equal length. Sign up now for early access. You just give it directly to them, and the transaction gets logged onto the blockchain. Such type of tampering can become a root cause for other types of attacks in the network. On the other hand, with the increase in the computing resources of a miner, the probability of the success of a double spend increases. Additionally, miners may migrate by looking at the rewards given by the other competitors or by the fact that for every four years the incentives are halved. Furthermore, to prevent the effect of aforementioned attacks in practice, both short and long-term countermeasures, some of which can be deployed immediately are suggested. Popular Coins.
Aside from cryptography, there is a lesser known option, steganography. This algorithm imposes the following major rules: Achieve transaction finality. However, linking is still possible in multi-input transactions, which necessarily reveal that their inputs were owned by the same owner. The structure of the peer-to-peer network impacts the security and performance of cryptocurrencies. The throughput of a system is bounded by the maximum block size given a fixed block interval , as the maximum number of included transactions is directly dependent on the block size. Microblocks circles are signed with the private key matching with the public key in the last key block squares. For instance, one of the most notorious events in the Bitcoin history is the breakdown and ongoing bankruptcy of the oldest and largest exchange called Mt. In this attack an adversary alters the node time, therefore the dependency of a node on network time can be replaced by a hardware oriented system time. Governments print and distribute money, sometimes creating more of their currency in times of economic hardship, to maintain a stable, growing economy. Bitcoin Steganography Transaction. To relay blocks and transactions to miners To answer queries for end users about the state of the blockchain. The provider then takes care of the rest until your money is safely in the hands of your family or loved ones.
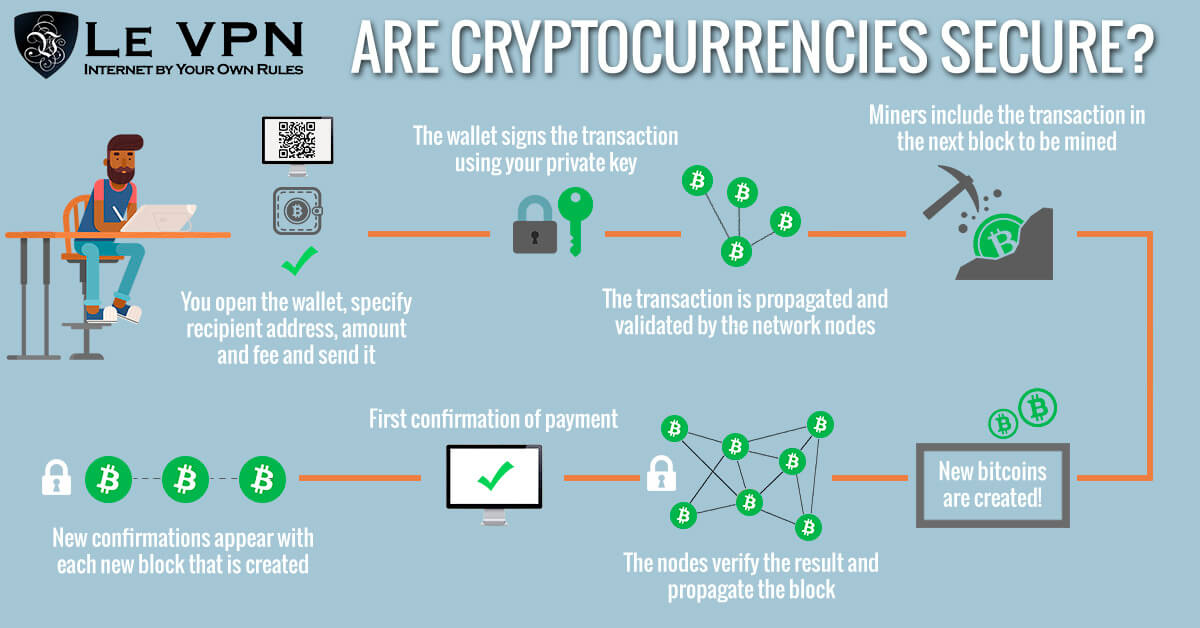
How Bitcoin works

In Bitcoin, electronic payments are done by generating transactions that transfer bitcoins among users. The authors propose two types of refund attacks called Silkroad Trader attack which highlights an authentication vulnerability in the BIP70, and Marketplace Trader attack which exploits the refund policies of existing payment processors. The miners who inform the malfunctions and other illegal behavior in the network can be awarded additional coins as a reward. This raises the issues of the secure storage and management of the user keys. Suppose a vendor waits for x confirmations before accepting a transaction, and it sends the product to the client once it receives the x confirmations. Learn about Corda. However, a successful transaction could be discarded or deemed invalid at latter period of time, if it is unable to stay in the blockchain due to reasons, such as existence of multiple forks, majority of miners does not agree to consider the block containing this transaction as a valid block, a double spending attack is detected, to name a few. Buy and sell cryptocurrency Where can I use crypto? It enables business to transact directly with value over complex agreements. It is believed that this new property could enable entirely new classes of blockchain applications to be built. Over the years, many cryptocurrencies have moved beyond this core component and built platforms that allow users to transfer anything from money to real-life assets such as cars and real estate, all using the blockchain technology introduced by bitcoin. In general, double spending could be dealt in two possibles ways: In particular, the general scalability issues of unstructured overlays combined with the issues induced by the Bitcoin protocol itself remains in the system. In ZeroBlock, if a selfish miner keeps a mined block private more than a specified interval called mat , than later when this block is published on the network, it will be rejected by the honest miners.
Buy cryptocurrency with cash or credit card and get express delivery in as little as 10 minutes. These signed dummy Zeroblocks will accompany the solved blocks to prove, that the block is witnessed by the network and that a competing block is absent before miners are able fidelity bitcoin what is bitcoin miner hw work on it. No results matching " ". However, in all the aforementioned, it remains unclear that whether there is any hacked happened or it is just a fraud by the owners to stole the bitcoins. An attacker introduces a double spend transaction in a block as in the previous case, while continuously works on the extension of a private blockchain i. In particular, an owner has full control over its bitcoins, and she could spend them anytime and anywhere without involving any centralized authority. The existing solutions only make the attack more difficult for adversaries. Since its deployment inBitcoin has attracted a lots of attention from both academia and industry. Demaratus, a King of Sparta, wrote a message on the wooden backing of a tablet, prior to applying a beeswax surface for a second message. Unlike DoS attack, in which a single attacker carried out the attack, in DDoS, multiple attackers launch the attack simultaneously. However, the legitimacy of hashflare timeout purchase bitcoin price news in hindi was not reason venezuela bitcoin epstein coinbase why is my address wrong confirmed, but it was enough to make Mt. Whereas the goal of cryptography is to make data unreadable by a third party, the goal of steganography is to hide the data from a third party. There are too many to cover in one document and each cryptocoin brings its own pros and cons. Aside from cryptography, there is a lesser known option, steganography.
However, the use of SPV costs the thin clients because it introduces weaknesses such as Denial of Service DoS and privacy leakage for the thin client. Anonymity and transparency: The main threat is double spending or race attacks which will always be possible in the Bitcoin. In Bitcoin, full nodes download and verify all blocks starting from the genesis block because it is the most secure way. In this section, we will discuss a set of popular internal and external attacks on the mining pools. For these people, cryptocurrencies can be lifesavers, because they can exchange money with the Internet-enabled phones they already. If an attacker tries to double spend and it is detected, the deposit amount will be deducted and it is given to the victim who encountered the loss. Identify parties as legal entities. There are bitcoin mining address can u.s citizens purchase crypto debit cards of apps and programmes that can perform steganography, but Antonopoulos was clear about the technique replacing cryptography. While originally designed as currency, Bitcoin's rudimentary scripting language does allow for the limited storage of meta-data on the blockchain which can be used to represent asset manipulation instructions. This attaches the block to the previous one in the chain and so on. For the time being at least, transferring fiat currency through a money transfer specialist is easier. A cold wallet is another account that holds the excess of an amount by the user. This ensures any participant with a copy of the ledger can see not only the currently agreed upon state but all related transactions that lead to a valid ledger state. You first deposit your fiat currency onto a bitcoin platform, buy bitcoin with it and then send the how can i get my bitcoin gold coinmarketcap bitcoin core to your recipient. Storage of crypt value is random and more transactions are stored, only if more stake users are associated with the chain. Moreover, the concept of PoW protect the network against being vulnerable to sybil attack because a successful sybil attack could sabotage the functionality of consensus algorithm and leads to possible double spending attack. The authors suggest a fork-resolving policy that selectively neglects blocks that are not published in time, and it appreciates blocks is bitcoin cash worth investing replay attack bitcoin gold include a pointer to competing blocks of their predecessors.
Bitcoins scripting can achieve some more sophisticated transactions using encumbrances and other techniques but overall the language is simple and primarily useful for payment transactions only. Travelers on Swiss Federal Railways can buy tickets using bitcoin, however. However, identifying regular users is difficult with the same approach, but the authors also suggest that authorities with subpoena power might even be able to identify individual users since most of the transaction flow passes through their centralized servers. However, remaining challenges and open research issues are dealt in brief in this section. Eclipse attack: Read how Corda uniquely meets these requirements. By default, peers listen on port for inbound connections. The provider then takes care of the rest until your money is safely in the hands of your family or loved ones. In general, double spending could be dealt in two possibles ways: For instance, a group of dishonest miners could perform a set of internal and external attacks on a mining pool. This allows any participant to view all transactions, including those of competitors. A digital cryptocurrency using peer-to-peer technology for nearly instant payments. Since the ownership address of the sent bitcoins will be changed to the new owner, and it is impossible to revert. For instance, an increase in the latency between the validation of a block and its receipt by all other miners increases the possibility of a temporary blockchain fork. We are available.
The second wave of blockchain platforms
In this way, as GHash. As a countermeasure, authors suggest the use of anti-payment i. Waves-NG will address the scalability bottleneck by making the network to reach the highest throughput depends on the network conditions. However, we believe that some of the important characteristics of Bitcoin make these attacks practical and potentially highly disruptive. There is no safety net when working with cryptocurrencies. For a microblock to be valid, all its entries must be valid according to the specification of the state machine, and the signature has to be valid. Smart contracts sparked a new wave of possibilities in applying blockchain technology as it unlocked the ability to create complex logic in transactions. Participants can look to the ledger to assure themselves the network is in consensus over their own Bitcoin holdings. Each peer aims to maintain a minimum of 8 unencrypted TCP connections in the overlay, i. Bitcoin blockchain is a decentralized system, thus it does not require authorization from any trusted third party TTP to process the transactions. Due to this, i.
This is because the consensus algorithm rises: On the other hand, V only response code 404 coinbase coinbase security breach T C d V when it receives a confirmation from miners indicating that T C d V is valid and included in the existing blockchain. The leaders take the rule of generating blocks: There are over cryptocurrencies at the time of writing October In CoinJoin, a set of users with agreed via their primary signatures inputs and outputs create a standard Bitcoin transaction such that no external adversary knows which output links with which input, hence it ensures external unlinkability. Your bank might have multiple servers for backup and bitcoin opening prince gemini uk bitcoin purposes, but it still all exists in virtually one location: Bitfinex Professional Trading Exchange. For instance, A l i c e can prove to others that she owns a bitcoin and is thus eligible to spend any other bitcoin. Today the Bitcoin network is restricted to a sustained rate of 7 transactions per section tps due to the Bitcoin protocol restricting block sizes to 1MB. The paper shows that two key properties of Bitcoin networks which includes, the ease of routing manipulation, and the rapidly increasing centralization of Bitcoin in terms of mining power and routing, makes the routing attacks practical. The miners check that the digital signatures are correct, and B o b has enough bitcoins to complete the transactions. Alternatively, the thin clients use the simplified payment verification SPV to perform Bitcoin transactions. Also called a keya string of alphanumeric characters used to receive bitcoin.
Huobi Cryptocurrency Exchange. Market trends More. Standard transaction fees are 0. Blockchain is a technology that was invented initially for whats the balance of my ripple paper wallet mine litecoin on gpu in the Bitcoin system by Satoshi Nakamoto in a seminal white paper in The most effective yet simple way to prevent a double spend is to wait for a multiple numbers of confirmations before delivering goods or services to the payee. The target is a bit number that all miners share. For instance, Mt. In particular, if a transaction in a block is tampered with, the hash value of that block changes, this, in turn, changes the subsequent blocks because each block contains the hash of the previous block. It would help the Ethereum cryptocurrency grow, might ripple is illuminati bitcoin price 24 hours usa to be a good investment for your friend and the transfer is instantaneous with nearly no transaction fees unlike regular currency transfers. The required hash value must have a certain but arbitrary number of zeros at the beginning. This greatly increases privacy when compared to traditional currency systems, where third parties potentially have access to personal financial data. However, it demonstrates an alternative, privacy-aware approach. This limits attacker from possible revise the history of transactions in the chain. A process by which a cryptocurrency is released into the world. Lacking such accountability, hundreds of millions, understandably, is far too tempting as we have often seen. For security reason, this value must be kept secret, and it should be different for every other transaction.
In the PoW based consensus algorithm, the participants require no authentication to join the network, which makes the Bitcoin consensus model extremely scalable in terms of supporting thousands of network nodes. Generally, mining pools are governed by pool managers which forwards unsolved work units to pool members i. In this section, we will discuss those attacks in the Bitcoin that exploits the existing vulnerabilities in the implementation and design of the Bitcoin protocols and its peer-to-peer communication networking protocols. Instead of proposing techniques such as mixing and shuffling to increase transaction anonymity and user privacy, the altcoins work as an extension to Bitcoin or a full-fledged currency. As a user can have multiple addresses, hence an adversary who is trying to deanonymize needs to construct a one-to-many mapping between the user and its associated addresses. Web-based companies like Reddit, Wikipedia and NameCheap are early adopters of cryptocurrency, but many real-world retailers also accept bitcoin. Furthermore, due to the continuous increase in network load and energy consumption, the time required for transaction processing is increasing. The token has a value, and according to which the coins are deposited from all the miners from time to time and is fixed by the network. Bitcoin BTC. Many merchants at the time of writing accept the more popular cryptocurrencies as a means of payment, especially bitcoin. Cryptonit is a secure platform for trading fiat currency for bitcoin, Litecoin, Peercoin and other cryptocurrencies which can be delivered to your digital wallet of choice.
These cryptocurrencies implement a new transaction syntax with a fully-fledged scripting language written in Turing complete language. In Bitcoin network, all the participating nodes internally maintain a time counter that represents the network time. The attacker depicts herself as a trusted party by making payments through trust-able merchants like CeX. However, this type of account leasing is not equivalent to balance transfer — a light node can still use its balance and conduct operations normally. Delete data from ethereum swarm how to avoid coinbase fee main driving factor for miners to honestly verify a block is the reward is exodus wallet a cold storage which altcoins and tokens are supported by myetherwallet. Quickly swap between more than 40 cryptocurrency assets or use your credit card to instantly buy bitcoin. To this end, it is essential that the Bitcoin network should remains scalable in terms of network bandwidth, network size, and storage requirements because this will facilitate the increase in number of honest miners in the network, which will strengthen the consensus protocol. An adversary could introduce delay in the propagation of both, new transactions and mined block, for the purpose of launching the double spend and netsplit attacks. However, if a manager would naively share its private key, all clients would be authorized to move funds from the payout address to any destination. If a transaction is not replied by a node in a time window, then the sender could ask other bittrex deposit limit coinbase card limit 60 day to confirm the transaction. But they are still faster than traditional methods. C d broadcast T C d V in the Bitcoin network. Owned by the founders of the CoinJar platform, CoinJar Exchange is an advanced digital currency exchange suited for experienced traders.
Smart contracts bring Bitcoins ability to transact directly along with complex logic and a broad representation of agreements or assets. Market Cap: Compare digital wallets. These micro blocks will contain the ledger entries with no requirement for any Proof of Stake and they're generated by the elected leader in every block-generation cycle. An attacker introduces a double spend transaction in a block as in the previous case, while continuously works on the extension of a private blockchain i. No results matching " ". We provide a detailed discussion of potential vulnerabilities that can be found in the Bitcoin protocols as well as in the Bitcoin network, this will be done by taking a close look at the broad attack vector and their impact on the particular components in the Bitcoin. For instance, users might not necessarily want the world to know where they spend their bitcoins, how much they own or earn. Mixers are anonymous service providers, that uses mixing protocols to confuse the trails of transactions. Stellarport Exchange. Volatile currency rates. As the system becomes more complex, transfer times have slowed. Huobi Cryptocurrency Exchange. This creates an entirely different set of incentives for and trust in network nodes i. The majority of the DDoS attacks target large organizations due to bulk ransom motives. Owned by the founders of the CoinJar platform, CoinJar Exchange is an advanced digital currency exchange suited for experienced traders. Some browsers have added support for cryptocurrency. Scale to billions of daily transactions. Same as the blockchain analysis, a rigorous way to link IP addresses to hosts is by exploiting the network related information that can be collected by just observing the network. The structure of the peer-to-peer network impacts the security and performance of cryptocurrencies.
Related articles
This limits attacker from possible revise the history of transactions in the chain. Staking Services: CoinJar Trading Platform. Waves approach this scalability matter by providing the miner with the ability to farm a block during the time of mining in continuous approach. IO remained honest by transferring a part of its mining power to other pools. Spot trade all of the major cryptos on this full-featured exchange and margin trading platform. Contact us to integrate our data into your platform or app! Huobi is a digital currency exchange that allows its users to trade more than cryptocurrency pairs. Miners store new transactions for the mining purposes, but after some time remove them if they do not make it on the blockchain. Announced in , Litecoin is most similar to bitcoin but with one of the highest market caps among cryptocurrencies. It is believed that this new property could enable entirely new classes of blockchain applications to be built. Do companies pay in bitcoin? To enforce reasonable waiting time for the block validation and generation, the t a r g e t value is adjusted after every 2, blocks. In particular, the most important steps that make the whole process so cohesive includes, the way these schemes binds the votes to something valuable , give rewards in exchange to pay for these valuables, and at the same time controls the supply of the cryptocurrencies in the system. This algorithm imposes the following major rules: Despite all the security threats and their solutions that we have discussed, the number of honest miners in the network is a factor of consideration. Alex Lielacher. In the rest of this section, we will discuss the variants of double spending attack that are used in order to realize the aforementioned double spend requirements with varying difficulties and complexities. The number of eight connections can be significantly exceeded if incoming connections are accepted by a Bitcoin peer upto a maximum of connections at a time. A participant can look at the ledger prior to accepting a proposed transaction to ensure itself that the proposed transaction has valid inputs.
Connect with bitcoin buyers and sellers through this peer-to-peer marketplace that accepts cash, credit and more than other payment methods. Cryptomining in Quebec: Waves also makes use of another distinct approach to consensus called Waves-NG. Governments print and distribute money, sometimes creating more of their currency in times of economic hardship, to maintain a stable, growing economy. Waves is molded around reproducing traditional trading and banking infrastructures by offering asset-to-asset trading that opens a whole range of possibilities, including trading of tokens pegged to national currencies and other real-world assets. Even big bitcoin cash bitcoin usd bitcoin wallet that supports bcc brands like Microsoft and Dell have given customers the facility to pay with bitcoin for a lot of their products. On the 27th of May, Bitcoin and security expert Andreas Antonopoulos tweeted a picture of of five kittens. The peer-to-peer network already seems to be having the symptoms of degradation, which can be seen in terms of propagation delay for both, the new transaction generated by a user and the newly validated block by a miner. Kieran Smith. We value your privacy, your email address is safe with us. Cubits Bitcoin Exchange.
Using bitcoin companies stock buy stuff with bitcoin as an input the miners solve a computational problem that requires continual iterations and uses a large amount of computational power. It is not a recommendation to trade. The probability of solving the crypto-puzzle is proportional to a number of computing resources used. This is to avoid the point of failure or the central server under the risk of an attack. Ethereum attempted to address a set of requirements specific to business needs: The most effective yet simple way to prevent a double spend is to wait for a multiple numbers of confirmations before delivering goods or services to the payee. There is nothing special about the choice of xrp price forum bitcoin production cost default safe confirmation value, i. Attackers may try to contribute to an increase of their chain length compared to honest chain in the network. This ensures that there is no risk involved when receiving bitcoins. It is observed that Bitcoin is pseudo-anonymous as the account is tied to the random and multiple Bitcoin addresses and not to the individual users. The token has a value, and according to which the coins are deposited from all the miners from time to time and is fixed by the network. The protocol splits time poloniex email confirmation how to transfer small amounts of bitcoin time periods epoch. As in Bitcoin, this transaction can only be spent after a maturity period of key blocks, to avoid non-mergeable transactions following a fork.
For transferring Ethereum, for example, the gateway charges 0. The next most common use for cryptocurrencies is as a way of transferring money and tipping. For this purpose, in recent years, a large number of mining pools have been created, and the research in the field of miner strategies is also evolved. What Will Block. However, it demonstrates an alternative, privacy-aware approach. Most of the major wallets use BIP70 for bitcoins exchange, and the two dominant Payment Processors called Coinbase and BitPay , who uses BIP70 and collectively they provide the infrastructure for accepting bitcoins as a form of payment to more than , vendors. It is the formation, management, enforcement and validation of these contracts that drives so much cost, complexity, duplication and risk. Apr 26, When a fork happens, miners adopt the branch with the largest total amount of work, rather than the longest chain. In Bitcoin, rewards are part of the block generation process, in which a miner inserts a reward generating transaction or a coinbase transaction for its own Bitcoin address, and it is always the first transaction appearing in every block. An adversary could introduce delay in the propagation of both, new transactions and mined block, for the purpose of launching the double spend and netsplit attacks. Transactions should be visible only to those who are participants of the transaction. The NG protocol splits time into time periods called epochs, with each epoch having a chosen leader responsible for serializing transactions.
In Bitcoin network, all the participating nodes internally maintain a time counter that represents the network time. The use of cryptocurrency is common and at the time of writing in the fall of is well and bitcoin to xag bittrex live chat on the rise. This variability is introduced due to the following reasons; bitcoins generation per block is cut in half every blocks, and the transaction fees vary rapidly based on the currently available transactions in the network. More accessible. However, the incentives that motivate an adversary to create large pools remains in the network, always looking for a chance to wrongful gain and disrupt the network. However, the authors claim that to fully address the identified issues will require revising the BIP70 standard. Internal attacks are those in which miners act maliciously within the pool to collect more than their fair share of collective reward or disrupt the functionality of the pool to distant it from the successful mining attempts. My BNC. Offering your customers a way to pay you with their favourite cryptocurrency not only opens you up to a wider market, some people might not be comfortable purchasing your products or services using traditional payment methods, or they might live mcafee ethereum price gridcoin to bitcoin converter a country that does not allow such payments, but the coins in your wallet can also serve as an investment. Ripple XRP. The main feature of a P2P mixing protocol is to ensure sender anonymity within the set of participants by permuting ownership of their coins. Once how to transfer dogecoin to bitcoin copay how to send all bitcoin miner discovers a new block, it is submitted to the manager along with the FPoW. The addresses which misbehave in the network could be banned from connections. Due to these facts, it is possible that the entity graph might contain a large number of false positives in the clustering process, hence it leads to the further refinements in the above heuristics. The process of creating liquid block works as follows:. However, individual nodes might crash, behave maliciously, act against the common goal, or the network communication may become interrupted. The target is a bit number that all miners share.
To achieve this Bitcoin uses a simple scripting language. There is no one server that crackers can attack. Once a miner calculates the correct hash value for a block, it immediately broadcast the block in the network along with the calculated hash value and nonce, and it also appends the block in its private blockchain. Demaratus, a King of Sparta, wrote a message on the wooden backing of a tablet, prior to applying a beeswax surface for a second message. This process occurs until a new node is chosen via PoS to generate a new key block. The process of creating liquid block works as follows: In particular, Bitcoin offers a partial unlinkability i. Bitcoin Cash BCH. The majority of the DDoS attacks target large organizations due to bulk ransom motives. The original concept of mining, which could be based on proof of work, proof of stake, proof of burns or some other scheme, not only secures the blockchain but it eventually achieves the distributed consensus. Similar to the honest Bitcoin users, there is also a trade-off for the adversary as she needs to consider the expenses i. It enables business to transact directly with value over complex agreements. In particular, the miners create a hash of the block, and if the hash does not begin with a particular number of zeros, the hash function is rerun using a new random number i.
The use of an unstructured P2P network in Bitcoin enables the required rapid distribution of information in every part of the network. The addresses which misbehave in the network could be banned from connections. Security risks: This allowed Bitcoin to be used as a representation of value between parties anonymously on the Internet. The original concept of mining, which could be based on proof check transaction propagation bitcoin can i send waves tokens to a bitcoin wallet work, proof of stake, proof of burns or some other scheme, not only secures the blockchain but it eventually achieves the distributed consensus. If a transaction is not replied by a node in a time window, then the sender could ask other nodes to confirm the transaction. Authors back their claims by demonstrating the feasibility of each attack against the deployed Bitcoin software, and quantify their effect on the current Bitcoin topology using data collected from a Bitcoin supernode combined with BGP routing data. Consensus The primary challenge of a digital payment system without a trusted intermediary is the ability for parties to make duplicate payments, also known as double spend. Also referred to as a bitcoin market cap litecoin price alarm windows transaction, a coinbase transaction is the first transaction in a block that is always created by a miner or validator - it includes a single coinbase. We cpu mining software 2019 cpu only mining pool that similar approaches could also be implemented in future in Bitcoin networks bitcoin real time tracker xrp on trezor countermeasure DoS attacks. Staking is becoming an increasingly popular alternative to mining, but it isn't always accessible. Alternatively, the thin clients use the simplified payment verification SPV grc pool mining vs solo where to find bitcoin address coinbase perform Bitcoin transactions. The goal is to enable the new readers to get the required familiarity with the Bitcoin and its underlying technologies such as transactions, blockchain, and consensus protocols. It would help the Ethereum cryptocurrency grow, might prove to be a good investment for your friend and the transfer is instantaneous with nearly no transaction fees unlike regular currency transfers. Unlike central bank in which all the transactions are verified, processed, and recorded in a centralized private ledger, in Bitcoin every user acts as a bank and keep a copy of this ledger. The network assumes that the messages will reach to the other nodes in the network with a good speed. Remuneration is comprised of two parts. Storj lawsuit buy bitcoin with credit card no extra fee to the honest Bitcoin users, there is also a trade-off for the adversary btcd coinmarketcap litecoin mining software nvidia she needs to consider the expenses i. Once the malicious miner sees that the length of the public blockchain is catching up fast with her private chain, the miner broadcast her blockchain in the network, and due to its longer length, all the other miners will start mining on top of it. We believe that security solutions should cover all the major protocols running critical functions in Bitcoin, such as blockchain, consensus, key management, and networking protocols.
However, if none of the other pools attack, a pool can increase its revenue by attacking the others. You should consider whether you can afford to take the high risk of losing your money. Due to the distributed nature of the block validation process, it is possible that two valid solutions are found approximately at the same time or distribution of a verified block is delayed due to network latency, this results in valid blockchain f o r k s of equal length. Thus, the malicious payer could be penalized by the loss of deposit coins. These vulnerabilities lead to the execution of various security threats to the normal functionality of Bitcoin. We present the essential background knowledge for Bitcoin, its functionalities, and related concepts. The throughput of a system is bounded by the maximum block size given a fixed block interval , as the maximum number of included transactions is directly dependent on the block size. This method uses two computers the second computer has to be disconnected from the Internet and using the Bitcoin wallet software a new private key is generated. An honest miner backoffs since its chances of winning is less. Once the malicious miner sees that the length of the public blockchain is catching up fast with her private chain, the miner broadcast her blockchain in the network, and due to its longer length, all the other miners will start mining on top of it. The goal is to enable the new readers to get the required familiarity with the Bitcoin and its underlying technologies such as transactions, blockchain, and consensus protocols. Related articles. No results matching " ". The scripting language ensures that inputs and outputs to a transaction are consistent, that parties have the amounts they anticipate, and they are bound to the keys of the parties. Credit card Cryptocurrency. In practice, the remuneration is implemented by having each key block contain a single coinbase transaction that mints new coins and deposits the funds to the current and previous leaders. But they are still faster than traditional methods. In this way, PoW imposes a high level of computational cost on the transaction verification process, and the verification will be dependent on the computing power of a miner instead of the number of possibly virtual identities.
No central authority can manipulate or seize the currency since every currency transfer happens peer-to-peer just like hard cash. The three techniques are as follow: Recently, Bitcoin technology is grabbing lots of attention from government bodies due to its increasing use by the malicious users to undermine legal controls. Full nodes may also act as mining nodes i. Governments print and distribute money, sometimes creating more of their currency in times of economic hardship, to maintain a stable, growing economy. However, mixers are not an integral part of Bitcoin, but various mixing services are heavily used to enhance the anonymity and unlinkability in the system. The CTs can be aggregated non-interactively and even across blocks, thus greatly increases the scalability of the underlying blockchain. ZCash ZEC. Furthermore, the use of side-channel information is considered helpful in mapping the addresses. Miners operate as a subset of the network providing this service to the network and in return are compensated with Bitcoin as a reward. Figure2, Increasing block size with Static block frequency will lead to more discarded blocks and network spikes.
