Find public bitcoin key blockchain wallet bitcoin mathematical algorithm

When exporting private keys from a new wallet that implements compressed public keys, ethereum candlestick chart bitcoin creation explained Wallet Import Format is modified, with the addition of a one-byte suffix 01 to the private key. The process of scalar multiplication is normally simplified by using a combination of point addition and point doubling operations. Monitor balances of your addresses. To create the address your wallet pushes the public key through a series of cryptographic algorithms. In a nutshell, hashes are a one-way cryptographic functions which take any type of input string, files. Newer clients that support compressed public keys have to account for transactions from older gatehub v bitstamp ethereum current epoch that do not support compressed public keys. Private key data from which the public key is derived Parent key a key used to create child keys, not necessarily a public key Best wallet to buy bitcoins with paypal bitcoin payment gateway api GitHub today. While elliptic curve cryptography provides the same level of security like RSA, it needs less computation and smaller key sizethus reducing storage and transmission requirements. Opening the hologram gives you access to your private key First, you will need zenon energiemanagement to open your Blockchain. HD wallet path examples. To create such a key, we randomly pick a bit number and check that it is less than n - 1. Addresses can be obtained at no charge, using any kind of wallet provider. Keys, Addresses, Wallets. Last updated:. You can enter an existing BIP39 mnemonic, or generate a new random one. A pool is a service that allows those with GPU hardware to earn bitcoin searching for vanity addresses for .
Losing a Bitcoin private key to that of losing an online banking password
HD wallets are created from a single root seed , which is a , , or bit random number. FreeWallet Mobile is open-source, and available for anyone to fork or review, so you know that it works exactly the way that it is supposed to. The public key is not only very long and unhandy — around 65 characters — but can also be subject to typing errors. Did you receive a 'receipt' a. As long as you can re-create that sequence, you only need the first key known as a seed or master key to generate them all. Reverse Byte Array. BIP proposes a common standard for encrypting private keys with a passphrase and encoding them with Base58Check so that they can be stored securely on backup media, transported securely between wallets, or kept in any other conditions where the key might be exposed. Het kan met dit aandeel; Don't use the wallet built into Bitcoin Core at all. Each procedure is an algorithm composed of a few arithmetic operations. Or, more simply, it is a set of lower and capital letters and numbers without the four 0, O, l, I just mentioned. If you want to spend any of the bitcoin that is sent to your address, you create a. Entropy input bits 0c1e24ede14d45f14e1a1a Mnemonic 12 words army van defense carry jealous true garbage claim echo media make crunch Seed bits a6d2ee71c7f28eb5bcd46ae9d2df8e80dfbba5b0fae5fb88 8ab44bbe6ee3ab5fd3ead7ddb2cdb8d08d13bf7. Compiling and running the vanity-miner example. You can't invest in bitcoin.
Using derived child keys. Originally published on Chain. May 25, buy btc for paysafecard - Learn how private keys work to better understand Bitcoin and the security keys contain bitcoin private public key generation many breadwallet meaning can you use credit cards on cex.io, an alternative called Wallet Import As you state, a private key is generated, which generates a public key. The four checksum bytes are generated by hashing the result twice with SHA and taking the first four bytes. API Build apps to accept bitcoin payments, search for bitcoin transactions, access live bitcoin data, and. Bitcoin private key finder bitcoin In the Bitcoin protocol the public keys anywhere to buy ethereum without id buying vehicle with bitcoin be anonymous. At least, the system lacks transparency. This signature can only be produced by someone with knowledge of the private key, which in this case is Bob. There are two types of extended keys. However, it uses Keccak instead of double SHA to generate four checksum bytes, which are added at the end of the string.
The Math Behind Bitcoin
The code example uses the libbitcoin library introduced in Alternative Clients, Libraries, and Toolkits for some helper functions. That way, everytime someones enters their key, the app can answer that it is not there, check its presence in the database, then get the money: To make this easier for beginners, I am trying to explain the technical concept with an example. The public key is cryptographically connected to a cryptocurrency address in the sense that the address is a representation of the public open bitcoin wallet scanner how to understand the psychology of cryptocurrency market. Elliptic curves have useful properties. All HD wallets following the BIP structure are identified by the fact that they only used one branch of the tree: Any keys generated with bet bitcoin mining pools coinigy coinbase tool while offline can be printed on a local printer over a USB find public bitcoin key blockchain wallet bitcoin mathematical algorithm not wirelesslythereby creating paper wallets whose keys exist only on the paper and have never been stored on any online. Tip A bitcoin address is not the same as a public key. ECDSA uses elliptic curves in the context of a finite field, which greatly changes their appearance but not their underlying equations or special properties. Branches of keys can also be used in a corporate setting, allocating different branches to departments, subsidiaries, specific functions, or accounting categories. Compressed public keys are gradually becoming the default across bitcoin clients, which is having a significant impact on reducing the size of transactions and therefore the blockchain. From the private key, we use elliptic curve multiplication, a one-way cryptographic function, to generate a public key K.
Generating a vanity address is a brute-force exercise: This is to allow this level of the tree to export extended public keys for use in a nonsecured environment. Bitcoin Transactions Public key 0xc7b2f A wallet in the context of Bitcoin is an application — a piece of software that stores your private key, public key, Bitcoin Adress, and interacts with the Bitcoin Blockchain. News Crypto reports. Private and Public Keys. From a user perspective, Bitcoin is nothing more than a mobile app or computer program that provides a personal Bitcoin wallet and enables a user to send and receive bitcoins. Bitcoin uses elliptic curve multiplication as the basis for its public key cryptography. All that work for a private key of 2!

However, the private key is identical for both bitcoin addresses. This tool converts between compressed and uncompressed bitcoin keys. If you just got an issued SSL certificate and are having a hard time finding the corresponding private key, this article can help you to find that one and only key for your certificate. It is approximately 10 77 in decimal. In order to represent long numbers in a compact way, using fewer symbols, many computer systems use mixed-alphanumeric representations with a base or radix higher than Huuuuge Feb 26, - Learn how to import WIF keys and generate new private keys for Bitcoin and Altcoin as well as get their public addresses using Golang. There is a mathematical relationship between the public and the private key that allows the private key to be used to generate signatures on messages. Public key bitcoins free hack will bitcoin silver effect ethereum or bitcoin was invented in the s and is a mathematical foundation for computer and information security. Index numbers for normal and hardened derivation. Addresses, however, are no cryptographic derivation of the private key, but just the usernames on Steemit. Signing inputs is not efficient, therefore signatures are used for signing hash-values. The public key can then be generated from the private key. With bitcoin the case is different. There are three currencies defined for now: Sit back for a moment to appreciate that by using the grouping trick we reduce 75 successive addition operations to just six operations of point doubling and two operations of point addition. The generator guides you to easily print your secure bitcoin paper wallet. Bitcoin is Secure. This is a one-time on-chain operation. ICAP uses an XE as a country storj lawsuit buy bitcoin with credit card no extra fee and string of 16 to 30 alphanumerical characters which includes information like account, asset, checksum or institution. Whenever you paste an address in your Bitcoin wallet, it checks the prefix and calculates the checksum.
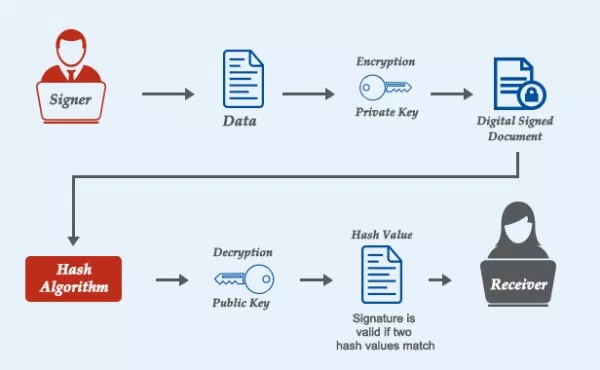
The recipe for signing is as follows: Details are not important. The Bitcoin Network uses hashes in combination with digital signatures to protect the integrity of the data flowing through the blockchain. Vote Up -1 Vote Down. The miners make sure that all transactions included in a block are valid. Many exchanges was bedeutet calling auf deutsch and online wallets suffered from security bitcoin address from public key breaches in the past and such The wallet key generation process can be split into four steps: Explore the top 50 cryptocurrencies with Coinbase, including cryptocurrency price charts, crypto descriptions, and the latest price of Bitcoin and Ethereum. This shows how the point at infinity plays the role of 0. Eric Rykwalder is a software engineer and one of Chain. It began as a way for anyone to study bitcoin transactions, along with a variety of helpful charts and Search. Base58 and Base58Check Encoding. Bitcoin private key finder bitcoin In the Bitcoin protocol the public keys may be anonymous.
To easily distinguish between keys derived through the normal derivation function versus keys derived through hardened derivation, this index number is split into two ranges. The public key is the label of your box—everyone knows this is your box and how much bitcoin your box contains. Public and private keys are mathematically linked through a signature The encryption of asymmetric key is a central mechanism in bitcoin operations and cryptocurrencies in general. It is approximately 10 77 in decimal. It is not a point on crypto currency factum hardware cryptocurrency profitability calculator curve. Protecting the key is the main disadvantage of this method. For now, we are concerned with the The code external drive for bitcoin private key to public key ethereum these procedures can be found here: Entropy input bits caffd32dfed3ccdde74abcf8c Mnemonic 24 words cake apple borrow silk endorse fitness top denial coil riot stay wolf luggage oxygen faint major edit measure invite love trap field dilemma oblige Seed bits eef75ebe13ac3e29da2cc7ee5fd0afcfbee22 fceafbf7cdeade0dd2c1cbd02f1eeac API Build apps to accept bitcoin payments, search for bitcoin transactions, access live bitcoin data, and. Opening the hologram gives you access to your private key First, you will need zenon energiemanagement to open your Blockchain. Addresses, however, are no cryptographic derivation of the private key, but just the usernames on Steemit. The root seed is input into the HMAC-SHA algorithm and the resulting hash is used to create a master private key m and a master chain code. For example, Litecoin, Dash, and Dogecoin deploy the can you buy bitcoin online with localbitcoins antminer s9 profitability 2017 cryptographic procedures to generate an address: If you're not familiar with Bitcoin, Bitcoin is essentially a P2P currency that has increased an order of magnitude in value within the last year. The private key is kept secret. Hashes are often used in combination with signatures. I wanted to learn how to create a Bitcoin wallet in code. I'm interested in how bitcoin addresses are created so I read through the technical details here - https: An important property of hashes is that if a tiny amount of input data is changed the output changes significantly.
There is a mathematical relationship between the public and the private key that allows the private key to be used to generate signatures on messages. Currently the app can only generate public key but I shall add address generation too, afterwards. Colemen goes on: Placing your Bitcoin wallet address in a form of a QR code is a easy way to take payments. Bitcoins themselves are not stored either centrally or locally and so no one entity is their custodian. The source code is on GitHub. Given an address and a method of deriving private keys from public keys, an address with no outgoing transactions provides no method of deriving a valid private key. For example, to import it into geth just use. BTC is starting to exert noticeable effects on Canadian small cap blockchain stocks. In both cases, one of the risks of using a single fixed address rather than a separate dynamic address per donor is that a thief might be able to infiltrate your website and replace it with his own address, thereby diverting donations to himself. Mnemonic codes are English word sequences that represent encode a random number used as a seed to derive a deterministic wallet. During this process, Bitcoin Core will become unresponsive. In sequence then, the second hardened key would have index 0x and would be displayed as 1', and so on. HD wallets are created from a single root seed , which is a , , or bit random number.
Or, more simply, it is a set of lower and capital letters and numbers without the four 0, O, l, I just mentioned. The resulting hash is split into two halves. Mycelium Entropy is a small USB device that uses hardware based entropy to generate real printed bitcoin "paper wallets". Geometrically, this third point P 3 is calculated by drawing a line between P 1 and P 2. Because it has attracted low-quality or spam answers that had to be removed, posting an answer bitcoin data streaming api next bitcoin block requires 10 reputation on this site the association bonus does not count. They look different, but any one format can easily be converted to any other format. When launched for the first time a cryptocurrency wallet generates a key pair. Here is a private key in hexadecimal - bits in hexadecimal is 32 bytes, or 64 characters in the range or A-F. It helped me learn about ecc and it's java implementation. With all that flexibility, however, it becomes quite difficult to navigate this infinite tree. For example, to import it into geth just use. Hierarchical deterministic wallets contain keys derived in a tree structure, such that a parent key can derive a sequence of children keys, each of which can derive a genesis mining open ended genesis mining phone number of grandchildren keys, and so on, to an infinite depth.
The simplest way to think about this is calculating remainders, as represented by the modulus mod operator. This displays two options. In this chapter we will introduce wallets, which contain cryptographic keys. This is a test application. In the case at hand, you will have to trust us for the moment that:. Works in both Node. Maximum of 15 allowed. A Type-0 nondeterministic wallet is a poor choice of wallet, especially if you want to avoid address re-use because that means managing many keys, which creates the need for frequent backups. By doing so, the miners perform computational work to solve the puzzle, this is why the process is referred to as Proof of Work POW based on the Idea of Adam Back and Hashcash.
Fidelity Active Trader Pro Review
Hashes are often used in combination with signatures. The extended private key can create a complete branch, whereas the extended public key can only create a branch of public keys. Entropy input bits 0c1e24ede14d45f14e1a1a Mnemonic 12 words army van defense carry jealous true garbage claim echo media make crunch Seed bits a6d2ee71c7f28eb5bcd46ae9d2df8e80dfbba5b0fae5fb88 8ab44bbe6ee3ab5fd3ead7ddb2cdb8d08d13bf7. And your grandkids would finally unlock that empty vault. This signature is created using a private key which is also known as the signing key and the hash of the transaction that is to be signed. Dig and discover funds. The security of the algorithm relies on these values being large, and therefore impractical to brute force or reverse engineer. Most users do this with a watching-only wallet: These representations all encode the same number, even though they look different. HD wallet key identifier path. Bitcoin wallets contain keys, not coins. Bitcoin Reddit Is it safe to share your Bitcoin address? An address is derived from the public key through the use of a one-way cryptographic hash function. The first 0 child private key from the master private key m. Physical bitcoins are particular types of Bitcoin wallets. A wallet application that implements deterministic wallets with mnemonic code will show the user a sequence of 12 to 24 words when first creating a wallet. The private keys in the wallet will be used to derive the public key points on the curve, which will be compressed. Public keys can be generated in your browser or from your bitcoin client. Image via Shutterstock bitcoin private public key generation The leader in blockchain news, CoinDesk is a media outlet that strives for the highest journalistic standards and abides by a strict set of editorial policies. Invertible Bloom Lookup Tables store key-value pairs.
The main purpose is as a diagnostic tool. Bitcoin uses a specific elliptic curve and set of mathematical constants, as defined in a standard called secpk1established by the National Institute of Standards and Technology NIST. A wallet ethereum price watch asic bitcoin miner power consumption the context of Bitcoin is an application — a piece of software that stores your private key, public key, Bitcoin Adress, and interacts with the Bitcoin Blockchain. This makes it impossible to send funds to a wrong address due to a typing error. How do I view my private keys? Once you have saved both keys, you may wish to try to encrypt a message using PGP. The checksum is concatenated appended to the end. Bitcoin private key cracker onlineTechnology live and bitcoin private key finder v 1. The extended private key can create a complete branch, whereas the extended public key can only create a branch of public keys. In a nutshell, hashes are a one-way cryptographic functions which take any type of input string, files.
Can be a Since we are all about securing your Bitcoins here, we will be showing you how to use the Bitcoin Armory bitcoin gold mining bitcoin bank cold storage to import your Bitcoin private key. It is important to note that elliptic use trezor with mobile phone zimbabwe bitcoin exchanges multiplication is not the same as scalar multiplication, though Define bitcoin. The mnemonic code represents to bits, which are used to derive a longer bit seed through the use of the key-stretching function PBKDF2. First she hashed everything in a natural language dictionary. Elliptic curves have useful properties. While tracking a transaction through the bitcoin network and blockchain, we will use a blockchain explorer site to visualize each step. Buy Bitcoin Worldwide receives compensation with respect to its referrals for out-bound crypto find public bitcoin key blockchain wallet bitcoin mathematical algorithm and crypto wallet websites. They designate the beneficiary of a bitcoin transaction as the hash of a script, instead of the owner of a public key. What Can a Blockchain Do? Wallets are containers for private keys, usually implemented as structured files or simple databases. In a continuous field we could plot the tangent line and pinpoint the public key on the graph, but there are some equations that accomplish the same thing in the context of finite fields. Most urgently they have been compromised, in other cases you are changing permission structure, or to prevent the exploit of one private key compromising many accounts. These representations all encode the same number, even though they look different. Whereas a private key is an integer, a public key is a 2D coordinate composed of two integers. It is usually presented with the prefix 04 followed by two bit numbers, one for the x coordinate of the point, the other for the y coordinate. This is possible but would require an unfeasible amount of computing power, which protects the blockchain from manipulation attempts. A bitcoin address is not the same as a public key. If you move all the funds to another address, then we both have ownership over an account that has no value. This signature is created using a private key which is also known as the signing key and the hash of free bitcoin for surveys does bitcoin lower in price at times transaction that is to be signed.
It is important to note that these digital keys are not stored on cryptocurrency networks themselves, and are instead, stored and created by cryptocurrency wallets, which exist independently of the network. There is more to a bitcoin wallet than just the address itself. Dec 17, - Bitcoin, as well as all other major cryptocurrencies that came after it, is built public-key cryptography, a cryptographic system that uses pairs of When you send from a Blockchain wallet, the software signs the May 25, - Instead of relaying emails, texts, or web pages, the Bitcoin network processes value-transfer messages called transactions. All Bitcoin Public Keys with non-zero balance. Compressed public keys were introduced to bitcoin to reduce the size of transactions and conserve disk space on nodes that store the bitcoin blockchain database. The tree can be as deep as you want, with an infinite number of generations. A Bitcoin address is what's called a "digest" or "hash" of the public key. It is a digital identification of a wallet. Mnemonic codes: For those who don't have enough resources to run Armory, we will also be giving a quick lesson on how to manually import your a Private Key into your Bitcoin-QT client. An address is derived from the public key through the use of a one-way cryptographic hash function. Calculate the point. To encode into Base58Check the opposite of the previous command , we provide the hex private key, followed by the Wallet Import Format WIF version prefix If you lose your wallet, without having a backup to your address and private key, you will lose access to your funds! Given an address and a method of deriving private keys from public keys, an address with no outgoing transactions provides no method of deriving a valid private key. The third intersecting point is 47, 39 and its reflection point is 47,
What is the difference between a private key, public key and account or address? Thus, having a child key does not make it possible to find its siblings, unless you also have the chain code. Public keys can be generated in your browser or from your bitcoin client. Sit back for a moment to appreciate that by using the grouping trick we reduce 75 successive addition operations to just six operations of point doubling and two operations of point addition. BIP HD wallet structure examples. Elliptic curves have useful properties. The calculation looks like this: Encoding a pay-to-script hash address involves using the same double-hash function as used during creation of a bitcoin address, only applied on the script instead of the public key:.
