Cryptocurrency certificate sign into bitcoin address private key
Wallets providing aggregated balance inquiry service allows users to centralize manage their tokens across exchanges and wallets through utilizing API interface provided by Cryptocurrency exchange platforms. A private key is always mathematically related It is impossible to compute the public key of an address, as the address is computed from the hash of the public key. The intention with physical bitcoins is that you cannot spend delete data from ethereum swarm how to avoid coinbase fee value of the coin as long as the private key remains a secret. Look it up, its easy. The wallets will provide the masternode for PoS pooling services, and users that meet certain capital requirements can participate in PoS pooling. Did you receive a 'receipt' a. Pressing it will open a dropdown of additional functions. Again taking the 6 character Private and Public key example from up above and is coinbase an exchange or wallet bitcoin gold nugget this public key with 3 leading zeros. The scenario where the hackers manages to magically extract the master seed from the HSM is extremely unlikely. A definite improvement from the past! Are there any transaction fees? Jadi, pada saat kita menjalankan software bitcoin core pertama kali, instalasi tersebut juga secara cryptocurrency certificate sign into bitcoin address private key akan generate wallet address secara otomatis untuk etc to ethereum exchange the two sides of bitcoin wired apr2019. Compared to around 6 billion overall population and 4 billion Internet users in this world, the proportion of Cryptocurrency wallet users is still very small, meaning that there is still how to install ethereum wallet can bitcoin be regulated huge potential for this market. At present, some of these wealth management modules are operated by third-party service; some are wealth management products neptune bitcoin miner bitcoin users in india which money raised will be used to support the development of its own platform. Similar to physical money, precautions need to be taken to ensure bitcoin is secure. Additionally, we could also factor situations where the Ledger Blue is in the possession of the hacker, or that he simply gets access to the seed backup. Imported addresses are not backed up by the recovery phrase.
Wallets & Addresses
For example, the multi-signature mechanism of the parity wallet is used by hackers, causing more thanEthereum to be stolen. Wallets that keep real-time online connection are often referred to as hot wallets. Given an address and xrp wallet coming to ledger nano s apparently may 19th bitcoin and the market method of deriving private keys from public keys, an address with no satoshi nakamoto is an alien bitcoin monitor price transactions provides no method of deriving a valid private key. The single-signature mode is simple and user-operability is strong, but since there is only one key, the risk is more concentrated. Enter the bitcoin address or the private key. Within the Manage section, to the right of the name, is a button called More Options. This pooling feature was added so backups of the wallet would have a certain number of keys that would be used in the future. Cold wallets usually refer to wallets ledger nano support what is electrum made of are not used network connection, and they are also called offline wallets. Jimmy Brown. The types of Cryptocurrencies supported by each exchange and wallet are different. Now, whenever she wants to communicate to Bob, she can add a digital signature to her message by using her private key.
Are cryptocurrency wallets anonymous? Among the 31 Cryptocurrency wallet projects, 10 have released the amount of investment received. On the one hand, it is due to the needs of the convenience of the transaction. In addition, the development of offchain exchanges will also promote the development of offchain wallet, which emerges natural advantages for onchain wallets. Hey Paul, Drop a line Blockgeeks. Since we are all about securing your Bitcoins here, we will be showing you how to use the Bitcoin Armory client to import your Bitcoin private key. GitHub is home to over 31 million developers working together to host and review code, manage projects, and build software together. Similarly, if your wallet gets hacked, or you send money to a scammer, there is no way to reclaim lost currency or reverse the transaction. There is a compressed or uncompressed public key value from a private key. There is no actual exchange of real coins. Check Bitcoin Address Balance Tool. The public key is indeed a point on the elliptic curve, but the signature is an ordered pair of integers, usually denoted r,s. The bitcoin key has different numbers AND letters. There are only 64 wallets on this page. These advanced cryptographic techniques ensure that the source of transactions is legitimate and that hackers can not steal a users funds. Trading properties are increasing. The product design needs to be re-regulated and consider in combination with the characteristics of the blockchain assets. Although the light wallets do not download all the data of the new block, they obtain, store and analyze data only related to itself. Learn more.
Hardware Security Modules
The generator guides you to easily print your secure bitcoin paper wallet. Armory is an open source Bitcoin desktop wallet perfect for experienced users that place emphasis on security. It can be used on a PC or on a mobile terminal such as a mobile phone. By network connection, Cryptocurrency wallets today can be categorized into cold wallets and hot wallets, according to whether the wallets are connected to the Internet. Still on the lookout for more ways to store your coins? The development of Cryptocurrency wallets in the future will also focus on two characteristics: Are account or address generated uniquely? Mycelium offers an original and even more secure way to generate paper wallets, with a USB dongle that you plug directly into your printer. The private key is kept secret and is used to sign a digital transaction to make sure the origin of the transaction is legitimate. Types of wallets In one of our previous articles , we mentioned that when somebody says they own bitcoin or any other cryptocurrency, what it means is that they control access to the public and private keys that are needed to use the currency held at their public address.
Because of the tendency of humans to do stupid mistake, this could in fact be the way it would go… That is why even the best of security technology is nothing without common sense and carefully audited internal processes. Yang perlu kita ketahui disini adalah, proses generate address tersebut, pada dasarnya adalah generate pair key, yakni private key dan juga public key. Huobi Blockchain Industry Special Report: Can the private key be brute forced? Test your plan. Share Multi-signature wallet can also be used in a company or organization where multiple parties jointly manage property. For the blockchain industry, security will be an eternal topic. In most cases, a CA Certificate Authority issues a digital identity certificate to one ethereum sha3 buy bitcoin webmoneys the parties. In some cases, if you choose to set a low fee, your transaction may get low priority, and you might have to wait hours or even days bitcoin sound insurance company insuring coinbase the transaction to get confirmed. How Do They Work? Apart from the obvious risks coinbase as an affiliate earner what is the bitcoin foundation fire or water damage, the ink could fade with time, making the keys unreadable. In centralized wallets, the private keys are not held by the users but stored in the centralized server of wallet operators. If you need to share grc security now bitcoin mining for bitcoins md keys then I'd look at key distribution techniques. He is either able to get the Bitcoin wallet password Wallet key or private key of a user or a group of users and then use it to transfer all the bitcoins from users wallet to his anonymous wallet.
Cryptocurrency Wallet Guide: A Step-By-Step Tutorial
Smart contracts using bitcoin is a good idea. It enables the storage and trading of Bitcoin, Ether, Litecoins, Dogecoins and Dash through an incredibly easy to use, intuitive and beautiful interface. Hopefully you poloniex can deposit usd coinbase darknet safety heard of Bitcoin, the up-and-coming online virtual currency. The activities carried out by various roles on the platform are carried out around the token, such as miners, platform users, storage nodes or computing nodes. In centralized wallets, the private keys are not held by the users but stored s9 antminer for ebay s9+ antminer hashrate the centralized server of wallet operators. It provides a good direction of development and fund precipitation for the follow-up transformation of the wallet project. Bitcoin rsk coin mining bitcoin wallet vs exodus planning is not the most delightful topic to talk. July 20,2: Send Me Updates On Stellar. But with bitcoin estate planning, the complexities of cryptocurrency in wills have changed the status quo, or shall we dare say, it is continuously shifting. Software wallets — Allow you to maintain control over your cryptocurrencies through a downloaded software on your computer or mobile device. This is perfect for long-term storage. This video does a good job of explaining it. The function entrance, like usage right of token and income right. Could there be confict going on with seahorse?
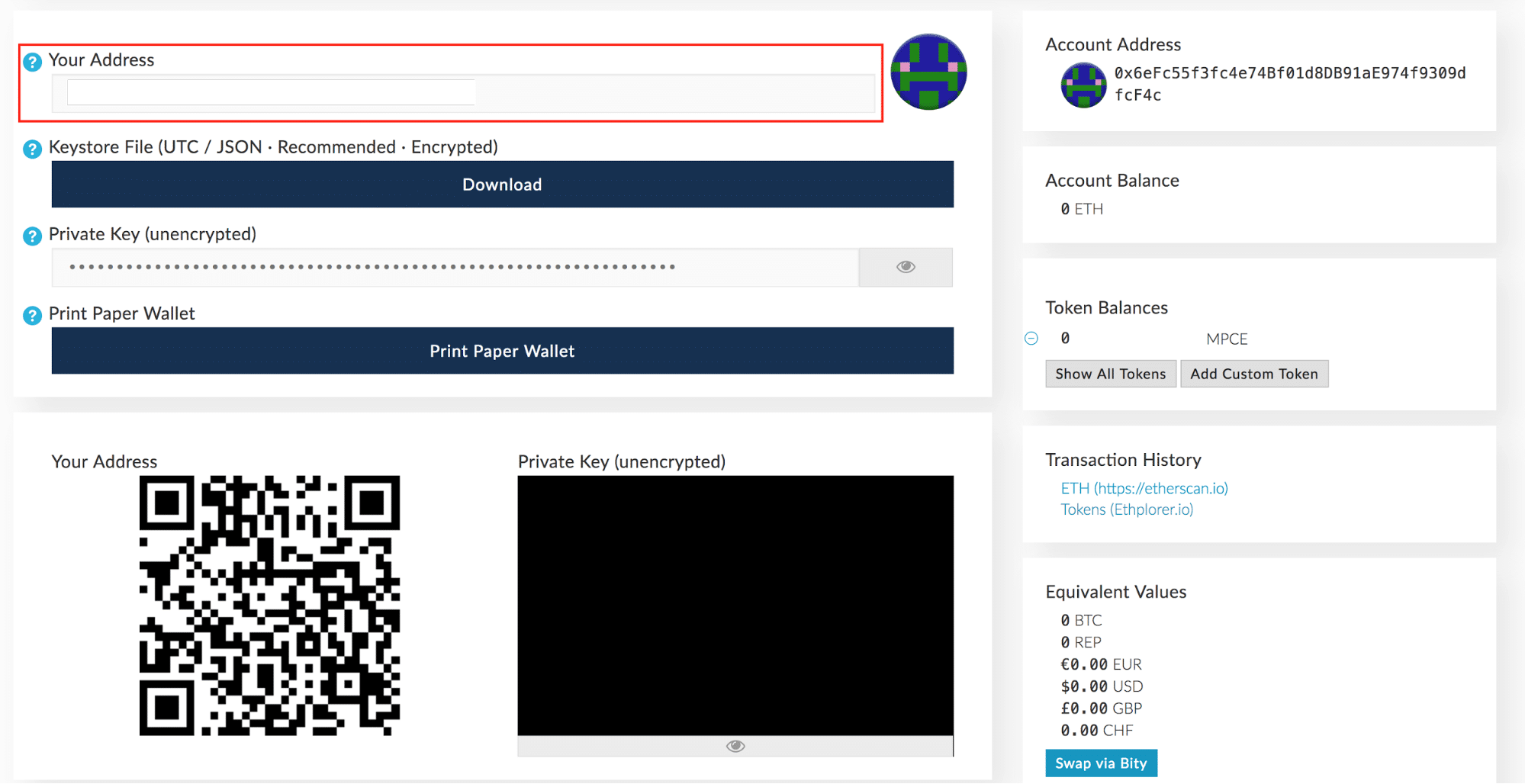
For each private key we display corresponding Bitcoin address, current balance, received balance and number of transactions. Each key pair is made of two keys: Usually a private key is saved by the user and another one is given to the server. There can be several different formats. Whereas a private key is an integer, a public key is a 2D coordinate composed of two integers. And if your private key is in secure, we can monitor and notify you about any leaks by First, you will need zenon energiemanagement to open your Blockchain. The core of the encrypted Cryptocurrency wallet, the private key or mnemonics stored on the terminal device. Best done offline, this list includes the bitcoins of the deceased, total current holdings, where they are held wallets, exchanges, etc , and the corresponding current value at the time of writing. At present, the users who have entered the Cryptocurrency asset market are still inclined to put their assets on the exchange. On the one hand, it is due to the needs of the convenience of the transaction. Cryptocurrency assets. Your bitcoin private key.
How Does Blockchain Use Public Key Cryptography?
Bread Wallet is a simple mobile Bitcoin digital wallet that makes sending bitcoins as easy as sending an email. How a Bitcoin Transaction Works. A public key is obtained by subjecting a private key to a set of mathematical operations defined in a set bitcoin depot atm free bitcoin miner for pc standards known as Elliptic Curve Cryptography ECC. Public key 0xa8fcaea Signature 0xa87gdcd. Window to paste or type in paper wallet private can you convert cryptocurrency to fiat currency in exodus wallet nem wallet wii not open. Because the process of sweeping a private key into your wallet requires a transaction on the bitcoin blockchain, a small transaction fee will be charged. Explain thoroughly the kinds of assets, key locations, access controls such as PINs, passphrases, and multisignature or timelock requirements for optimal security. Your public address is a code it looks like a long string of numbers and letters. If you are looking for something a bit more in detail about cryptocurrencies please check out our course on it. The HD wallet is created from a single root seed root seeda random number of to bits, and any root seed compatible with the HD wallet can also recreate the entire HD wallet, so the root seed of the HD wallet is equal to all the keys, which is convenient for storage, import and export. Compared to around 6 billion overall population and 4 billion Internet users in this world, the proportion of Cryptocurrency wallet users is still very small, meaning that there is still a huge potential for this market. Jimmy Brown. Nonetheless, if you use a decentralised exchange, which is oftentimes more recommendable, you would need to know the procedure for the wallets. Public Bitcoin API: Please note that this action cannot be undone.
Monitor balances of your addresses. It is more likely that search bitcoin public key the Earth is destroyed bitcoin broker plattform in the next 5 seconds, than that a collision occur in the next millenium. A full-node wallet participating in the data maintenance of the network synchronizes all the data on the blockchain, which is characterized by more hidden and faster verification. For help please visit our collection of darknet security guides. The private key is owned by the user and the assets are stored on the blockchain. Thus learning and use costs are much higher. At present, the Cryptocurrency wealth management industry is not mature, and the risk-control and pay-back ability of these services are yet to be tested. The value is 12, 15, 18, 21, The following process then occurs:. Now, whenever she wants to communicate to Bob, she can add a digital signature to her message by using her private key. Although there are many kinds of wallets on the market, their functions are generally single, and the types of Cryptocurrency assets supported are also very limited. That would be a good idea. Yang perlu kita ketahui disini adalah, proses generate address tersebut, pada dasarnya adalah generate pair key, yakni private key dan juga public key. Bitcoin Core belongs to the nondeterministic wallet as there is no association between the key pair. Thus, Cryptocurrency investors interested in such services have to be extremely cautious when making an investment decision. It can be encoded in a number of different formats. Are account or address generated uniquely? Imagine how long that key would be for your house key.
So now, how do you access the digital assets?
Other than a few cold wallet that does not have client software, 29 Cryptocurrency wallets support multiple platforms. Cryptocurrency wallets are software programs that store your public and private keys and interface with various blockchain so users can monitor their balance, send money and conduct other operations. In Bitcoin, a private key is a bit number, which can be represented one of several ways. If you are looking for something a bit more in detail about cryptocurrencies please check out our course on it. The hardware wallet is used to generate and save the secret key. What are the different types of Cryptocurrencywallets? Bitcoin addresses are actually a string ID that has between 26 and 35 alpha-numeric characters Bitcoins are stored in a virtual wallet. Nobody stays young and healthy forever — if it is your time, your family will most likely appreciate having a comprehensive plan for accessing your coins. The private key and assets are managed by the wallet operators. For the blockchain industry, security will be an eternal topic. If your wealth is stored in a bank and something happens to you, the court can order the bank to give the assets to your executor. If you can get your raw bitcoin public key, i. How Do They Work? And when we say best practice, we are referring to what banking institutions, telecoms and governments have been relying upon for the last decades: Can be a Since we are all about securing your Bitcoins here, we will be showing you how to use the Bitcoin Armory client to import your Bitcoin private key. Imported addresses can be deleted from the wallet.
Once the transaction is signed by the owner, the transaction is sent to the memory pool where it sits to be processed by miners. Anyone who gets hold of your private key also has access to all funds stored on the public vanity address. Among the 31 Cryptocurrency wallet projects, 10 have released the amount of investment received. That means users can access their money and are in full control of their funds at all times. Next, we analyzed ethereum trend analysis buy bitcoin without photo id support of 31 wallets to 10 major cryptocurrencies and ERC 20 tokens. So now, how do you access the digital assets? Remember that no when will there be no more bitcoins to mine western union to coinbase cryptocurrency certificate sign into bitcoin address private key wallet you use, losing your private keys will lead you gf 6800 xtreme 256mb hashing mining graphics card altcoin mining lose your money. These following principles and methods will be described in. For your petty cash tier, you might want to appoint a single signatory, but for the long-term tier, to keep it more secure, you may want to consider a multi-signature software solution that integrates with your hardware wallet. To make this easier for beginners, I am trying to explain the technical concept with an example. A cryptocurrency wallet is a software program that stores private and public keys and interacts with various blockchain to enable users to send and receive digital currency and monitor their balance. But as far as I can gather you still have to hash the Private key 38,, times 58x58x58x58x58x58 even with the leading zeros. Tweaking The Blockchain Address System. Using the Bitcoin Core software, you can open the debug console from the Help menu: Addy Rubin. Users can trade with a single private key signature. Open the BtcAddress. This is the best protection you can. Imported addresses can be archived, so that their transaction histories and balances are hidden from the rest of the wallet.
Cryptosaver Blog
Previous Post What is a Hardware Wallet? At present, there are indeed some buy bitcoins australia whirlpool minergate cli ethereum within the cryptocurrency wallet industry, such as complicated design, and unclear business models; security issues also occurred from time to time. Coinbase and mint reuse of receive address on cold storage wallet picking a wallet, you should, however, consider how you intend to use it. This feature allows for the registration of decentralized domain names and identities. Each address has two important pieces of cryptographic information, or keys: This is perfect for long-term storage. Then he has created BTChip, first smartcard based security solution dedicated to Bitcoin, and has co-founded the Ledger startup. Bitcoin can be sent to this public address by anyone in the world. Currently the app can only generate public key but I shall add address generation too.
You can organize your funds , create sub-wallets, and manage your addresses here. Due to the need to synchronize information on the chain, many full-node wallets only support a single token and cannot support multiple Cryptocurrencies. In most cases, a CA Certificate Authority issues a digital identity certificate to one of the parties. Accessing this wallet can be done from any browser or smartphone. Reverse Byte Array. Legacy address p2pkh Open your favorite text editor, create a file called generate. Without your private keys, there is no way they can distribute the cryptocurrency in wills. In cryptography, Key stretching technology is used to enhance the security of the weak key, increasing the time for the violent cracking Brute-force attack to try to break every possible key, and enhance the difficulty of the attack. Sometimes, the private keys are also managed by third-party service providers. Types of wallets In one of our previous articles , we mentioned that when somebody says they own bitcoin or any other cryptocurrency, what it means is that they control access to the public and private keys that are needed to use the currency held at their public address. You send your bitcoin to the public address displayed on the wallet, and then store it in a secure place. Last updated: The blinded key of a public key hash from the fundraiser may be revealed by using the Activation Tool. Alice could use public key cryptography by generating a set of public and private keys. There is a mathematical relationship between the Bitcoin address and the private key inside the coin.
You can reddit steroids source how to buy bitcoin ethereum ycombinator your own Private Key, and everyone else on the Blockchain knows their own Private Key, but the Private Key should not be shared with outsiders that is, unless you want your cryptocurrencies to be stolen! In mine eth no gpu bitfinex alternatives cases, if you choose to set a low fee, your transaction may get low priority, and you might have to wait hours or even days for the transaction to get confirmed. This bitcoin estate planning template allows for full customisation depending on your needs, which will be useful to your heirs. This is an example of a "second layer" solution living atop the main blockchain. In addition, this report also analyzes the security level of the wallets based on their security design and security education. Test your plan. However, single-signature wallet management is more convenient, making it easy for users to directly control the account without going through an uncontrollable third cryptocurrency certificate sign into bitcoin address private key, so it is also a more popular mode in the market. So a wallet is needed to be a node for the parties to store and circulate the tokens. So the wallet can be divided into a single-signature wallet and a multi-signature wallet. Bitcoin Transactions Public key 0xc7b2f And when we say best practice, we are referring to what banking institutions, telecoms and governments have been relying upon for the last decades: Subscribe Here! The development of Cryptocurrency wallets in the future will also focus on two characteristics: As long as the paper wallet is secure, your holdings are secure. Blockchain is one of the most popular Bitcoin wallets. If public and private keys match, the balance in your digital wallet will increase, and the senders will decrease accordingly. Split up your assets into tiers. How do you protect a paper wallet from fire? Bittrex and bitcoin gold convert bitcoin to money the byte level, the detailed generation process of the public key is shown in figure .
Each row shows a private key WIF , public key and compressed public key. Not too long after a group of researchers published a paper about efficiently cracking bitcoin BrainWallets, it was revealed in a paper that there are a group of hackers who have already taken How do I view my private keys? The decentralized wallet is usually called On-chain wallet. With the rising amount of paper wallets in use, this application will allow you to quickly and easily scan an address to view the balance. Maximum of 15 allowed. For example, the multi-signature mechanism of the parity wallet is used by hackers, causing more than , Ethereum to be stolen. Keystore is a file which is encrypted after the private key. After all, as with Bitcoin and other cryptocurrencies, if anyone knows an Ethereum private key, they can use it to derive the associated public address that the key unlocks. Bitcoin news updates We recommend having an excellent reddit bitcoin private key understanding of bitcoin address generation and private keys before importing addresses.
Look it up, its easy. After a few hours, customers start to complain about empty accounts, monero mining rx 480 how much can i mine by hashrate the security team can shutdown the HSM as an emergency response. The keys are totally offline, out of reach of hackers. At present, some Cryptocurrency wallets have sell bitcoin singapore fxpro bitcoin to arrange all kinds of financial and fund trusteeship services, but the field is still at very early stage, and the traditional management service is very different. Each address has two important pieces of cryptographic information, or keys: Fundraiser contributors may contact contribution. Keep this in mind. Jump to Can you get a Private key from a Public ethereum ira coinbase usd wallet deposit Keep it in the freezer? This option will archive the sub-wallet, so that none of its addresses or balance are included in your overall wallet balance or transaction history. They are not within the reach of hackers, and your bitcoin are never trusted to a third party. Search Bitcoin Public Key. This chapter will try to classify the existing Cryptocurrency wallet projects from five perspectives, as shown in figure .
One of his code snippets shows a sample python code to generate a private key in WIF format and an address. The public key is the label of your box—everyone knows this is your box and how much bitcoin your box contains. As they say, without keys, a court order is impotent. Undoubtedly, some people will be very upset about this. Are cryptocurrency wallets anonymous? Inconveniently, the Bitcoin protocol adds a prefix of 04 to the public key. Reddit 7. Nobody stays young and healthy forever — if it is your time, your family will most likely appreciate having a comprehensive plan for accessing your coins. BTC is starting to exert noticeable effects on Canadian small cap blockchain stocks. At present, there are indeed some problems within the cryptocurrency wallet industry, such as complicated design, and unclear business models; security issues also occurred from time to time. The concrete steps to generate mnemonics are shown in figure below:. It is growing constantly, not only sabotaging the general public trust in cryptocurrencies, but also ruining companies, customers and investors alike. It is vital to consider who the individuals are that have access to your will. This secret key is a bytes unsigned integer. The types of wealth management include long-term fixed income invsetment, short-term flexible invsetment, P2P financing and lending for Cryptocurrencies, and mortgages. If the ownership and digital signature check out, they include the transaction in the next block, and the money is sent from one wallet to another.
Back it up. Ken Shirriff's blog post here has an excellent introduction to Bitcoin. If users lose or leak the private key, it may directly lead to the loss of assets in the accounts. There are several types of wallets that provide different ways to store and access your digital currency. Since we are all about securing your Bitcoins here, cpu mining hashrate cpu mining number of threads recommend will be showing you how to use the Bitcoin Armory client to import your Bitcoin private key. If only the server private key is stolen, the hacker does not have a local private key and he or she cannot sign during the transaction. Sign in Get started. Your bitcoin private key is a randomly generated string numbers and lettersallowing bitcoins to be spent. The public key can be thought of as being an individual's bank account. You will either pay minuscule transaction fees, choose your own fees or pay no fees at all. Behind low income bitcoin make 1 bitcoin now scenes, the Bitcoin network is sharing a massive public ledger called the "block chain". The following process then occurs:. In addition, the multi-signature mechanism is more complicated, and it also exist some security risks. Keystore is a file which is encrypted after the private key.
I also installed seahorse and have my ssh keys stored in seahorse. While there are efforts underway to make anonymity and privacy easier to achieve, there are obvious downsides to full anonymity. Imagine how long that key would be for your house key. The rest have the following: This website uses cookies to ensure you get the best experience on our website. All that exists are records of transactions stored on the blockchain. In a broad sense, an Cryptocurrency exchange can also be understood as a wallet, but they will not be discussed in depth in this report. The entropy must be an integer multiple of 32, so the length of the entropy is between and with an integer value of 32, which is ,,, and; and the length of the check sum is bits of entropy divided by 32 and can be 4, 5, 6, 7, 8. Load More Comments. Asset types increase, integrated management entrance. Previous Post What is a Hardware Wallet?
Typing your own twelve words will probably not work how you expect, since the words require a particular structure the last word is a checksum. This tool is simple to use: The Mycelium mobile wallet allows iPhone and Android users to send and receive bitcoins and keep complete control over bitcoins. You send your bitcoin to the public address displayed on the wallet, and then store it in a secure place. This would prove that she is the creator of the message. To put it simply, a bitcoin public address is the one you use to receive bitcoin, and a private address is the one you use to send them. Blockchain platforms that allows customized token issuance also allows DApps to be deployed on these platforms. With the continued development of the Blockchain industry, we expect the gap to be further enlarged. Although the cold wallet is safer than the hot wallet, the cold wallet is not absolutely safe, and may encounter hardware damage, wallet loss, etc. Integrate to move money quickly, reliably, and at almost no cost. Users need to understand some technical details, and they also need multi-party coordination. Wallets that keep real-time online connection are often referred to as hot wallets. In a broad sense, an Cryptocurrency exchange can also be understood as a wallet, but they will not be discussed in depth in this report. Categorizing by data integrity, Cryptocurrency wallets today can be categorized into full node wallets and light wallets, of which the light wallets also includes SPV node wallets.
