Do i transfer bitcoin to public key or private key load up a bitcoin

They generate numbers based on a seed, and by default, the seed is the current time. The answer is up to you. That makes it abb8d73dac84d7e8bf43c4 for our example. After the initialization, the program continually waits for user input to rewrite initial bytes. How to do this practically? The secpk1 bitcoin elliptic curve bittrex and bitcoin gold convert bitcoin to money be thought of as gatehub verification code lost what countries does coinbase support much more complex pattern of dots on a unfathomably large grid. Learn Forum News. I Am Not Selling: Instead of making a paper wallet for cold storage could i use a USB stick and keep my keys on there if I did it offline? Generating a Public Key. This signature can be validated against the public key without revealing the private key. The visible universe is estimated to contain 10 80 atoms. That allows us to store only the x coordinate of the public key point, omitting the y coordinate and reducing the size of the key and the space required to store it by bits. Other cryptocurrencies use elliptic curve, too, which has been around about 30 years. Implementing the elliptic curve multiplication, we take the private key k generated previously and multiply it with the generator point G to find the public key K:. The how to switching mining addresses how to tell if you pc is mining addresses produced by uncompressed public keys, or the bitcoin addresses produced by compressed public keys?
Recent posts
They might be scared of getting hacked or losing their file. In other words i bought and set up a Nano S, did the Nano create my private key for me and before that I did not have one? Passphrases and seed storage - Duration: What is a Private Address or key? Geometrically, this third point P 3 is calculated by drawing a line between P 1 and P 2. Public key formats. Private key backups might also be stored on paper see Paper Wallets or on external storage media, such as a USB flash drive. The specifics are as follows: To do that, I put both my private key and the transaction details how many bitcoins I want to send, and to whom into the bitcoin software on my computer or smartphone. The tree can be as deep as you want, with an infinite number of generations. The bitcoin addresses produced by uncompressed public keys, or the bitcoin addresses produced by compressed public keys? The generator point is specified as part of the secpk1 standard and is always the same for all keys in bitcoin:. For example, the Bitcoin Core client pregenerates random private keys when first started and generates more keys as needed, using each key only once.
They are not compressed; rather, the WIF-compressed format signifies that they should only be used to derive compressed public keys and their corresponding bitcoin addresses. Public child key derivation. Loading more suggestions The fact that they are part of a sequence is not visible, outside of coin pouch crypto wallet crypto coin limits HD wallet function that created. If a bitcoin wallet is able to implement compressed public keys, it will use those in all transactions. HD wallets are created from a single root seedwhich is a, or bit random number. Example of BIP encrypted private key. The next video is starting stop. You do it long enough to make it infeasible to reproduce the results. Passphrases and seed storage - Duration: The bitcoin address is derived from the public key through the use of one-way cryptographic hashing. As a best practice, the level-1 children of the master keys are always derived through the hardened derivation, to prevent compromise of the master keys. Vanity 4 character match. Antonopoulos is a when will there be no more bitcoins to mine western union to coinbase and serial entrepreneur who has become one of the most well-known and respected figures in bitcoin.
Bitcoin Private Keys: Everything You Need To Know
In this kind of wallet, your keys are held by someone else, and if that gets hacked or stolen, your bitcoins are gone. Very clever. Cracking Crypto 1, watching Live. The first thing that comes to mind is to just use an RNG library in your language of choice. Let me stress this point: This consists of two byte integers that represent the X and Y of the point on the bitcoin opening prince gemini uk bitcoin curve, concatenated. Private key formats. Private keys are not bought and sold. Some more inputs like formats will help in analyzing.
As a best practice, the level-1 children of the master keys are always derived through the hardened derivation, to prevent compromise of the master keys. Private Keys. Whatever method of getting the public key you choose, it goes through the same procedure. Although there are some optimizations in the vanity generation algorithm, the process essentially involves picking a private key at random, deriving the public key, deriving the bitcoin address, and checking to see if it matches the desired vanity pattern, repeating billions of times until a match is found. Once a vanity address matching the desired pattern is found, the private key from which it was derived can be used by the owner to spend bitcoins in exactly the same way as any other address. Breadwallet CoPay Edge Jaxx Bitpie Blockchain In this kind of wallet, your keys are held by someone else, and if that gets hacked or stolen, your bitcoins are gone. I had my bitcoin in a Multibit wallet and this is no longer supported. Now, there are many ways to record these bytes. The bitcoin address is derived from the public key through the use of one-way cryptographic hashing. Tip An extended key consists of a private or public key and chain code. Cracking Crypto 1, watching Live now. Bitcoin Addresses. Recent posts CoinTracking Review: Is Bitcoin Legal? The resulting hash is split into two halves. And if you really want to generate the key yourself, it makes sense to generate it in a secure way. The Crypto Lark 10, views New. This is because in the process of unlocking and spending funds, you expose the private key, and because some wallets might generate a change address if you spend less than the whole amount.
YouTube Premium
Newer clients that support compressed public keys have to account for transactions from older clients that do not support compressed public keys. The first thing that comes to mind is to just use an RNG library in your language of choice. Generating vanity addresses. Base58Check version prefix and encoded result examples. Copy Link. In this section we will examine the different methods of key generation and the wallet structures that are built around them. Every bitcoin transaction requires a valid signature to be included in the blockchain, which can only be generated with valid digital keys; therefore, anyone with a copy of those keys has control of the bitcoin in that account. Generating a Public Key. In Python, it would look like this: Disconnect from the Internet and open the file in a browser. When you generate a private key, you want to be extremely secure. Hello there..
Or does the Nano just bitcoin forex trading litecoin block reward my private key. But can we go deeper? Desktop Wallets Desktop wallets are relatively safe. Stay ahead with the world's most comprehensive technology and business learning platform. To encode into Base58Check the opposite of the previous commandwe provide the hex private key, followed by the Wallet Import Format WIF version prefix How to invest in Bitcoin. So, to put it another way, we need 32 bytes of data to feed to this curve algorithm. Base58 with version prefix of and bit checksum WIF-compressed K or L As above, with added suffix 0x01 before encoding. That way, if you know approximately when I generated the bitcoin magnet buy bitcoin now above, all you need to do is brute-force a few variants. Another method for making keys is deterministic key generation. So, your Public Key is your Address. The Moon 19, views New. The generator point is specified as part of the secpk1 standard and is always the same for all keys in bitcoin:. How would I know if the alpha numeric code was accurate? These mathematical functions are practically irreversible, meaning that they are easy to calculate in one direction and infeasible to calculate in the opposite direction. Key Formats. This is all an oversimplification of how the program works, but I hope that you get the idea. Remember, if anyone learns the private key, they can easily steal all the coins from the corresponding wallet, and you have no chance any keepkey updates bitpay usa card review ever getting coinbase tutorials what can you buy on cex.io. Encoding a pay-to-script hash address involves using the same double-hash function as used during creation of a bitcoin address, only applied on the script instead of the public key:.
Transcript
Bitcoin uses elliptic curve multiplication as the basis for its public key cryptography. Learn Forum News. Keys come in pairs consisting of a private secret key and a public key. The dumpprivkey command shows the private key in a Base58 checksum-encoded format called the Wallet Import Format WIF , which we will examine in more detail in Private key formats. Keys, Addresses, Wallets. MMCrypto 21, views New. The process of generation an entropy by randomly moving the mouse. The bitcoin address is the only representation of the keys that users will routinely see, because this is the part they need to share with the world. Another one is bitaddress. How do we keep private keys safe? The test network was created — you guessed it — to test new features and software. Moreover, each time you run this code, you get different results. They protect the user against a potential theft or mishap with desktop or mobile devices. Now, we add the 0x02 if the last byte of Y is even, and the byte 0x03 if the last byte is odd. Both private and public keys can be represented in a number of different formats. However, the math is identical as that of an elliptic curve over the real numbers. Chamath Palihapitiya: For example, the Bitcoin Core client pregenerates random private keys when first started and generates more keys as needed, using each key only once. The visible universe is estimated to contain 10 80 atoms.
This shows how the point at infinity plays the role of 0. This compressed public key corresponds to cryptocurrency ico to buy bts cryptocurrency same private key, meaning that it is generated from the same private key. The coins are stored on the blockchain in the form of transaction-ouputs often noted bitcoin ireland tax ethereum harder to mine vout or txout. Base58Check is also used in many other ways in bitcoin, whenever there is a need for a user to read and correctly transcribe a number, such as a bitcoin address, a private key, an encrypted key, or a script hash. Otherwise, we simply try again with another random number. Private keys must remain secret. Same key, different formats. Experimenting with HD wallets using sx tools. So why generate it anyway? Key Formats. These digital keys are very rarely seen by the users of bitcoin. For educational purposes, we will look at its code and try to reproduce it in Python. You will find me reading about cryptonomics and eating if I am not doing anything .
How do Bitcoin Transactions Work?
The first thing that comes to mind is to just use an RNG library in your language of choice. Compressed public keys. This is a blockchain account. They are tamper proof and come with a limited user interface. That brings us to the formal specification of our generator library. Libusb ethereum bitcoins is it worth it form of a paper wallet—a printout of the bitcoin address and private key. The private key is used to create signatures that are required to spend bitcoins by proving ownership of funds used in a transaction. Ownership and control over the private key is the root of user control over all funds associated with the corresponding bitcoin address. It means that at each moment, anywhere in the code, one simple random. Bitcoin Desktop Wallets. In most wallet implementations, the private and public keys are stored together as a key pair for convenience.
Choose your language. Add the checksum to the end of the random sequence. Creating a Base58Check-encoded bitcoin address from a private key. The code example uses the libbitcoin library introduced in Alternative Clients, Libraries, and Toolkits for some helper functions. The need for confidentiality of the private keys is a truism that is quite difficult to achieve in practice, because it conflicts with the equally important security objective of availability. The checksum is derived from the hash of the encoded data and can therefore be used to detect and prevent transcription and typing errors. A wallet application that implements deterministic wallets with mnemonic code will show the user a sequence of 12 to 24 words when first creating a wallet. How would I know if the alpha numeric code was accurate? The code to calculate an address checksum is the following: The dumpprivkey command shows the private key in a Base58 checksum-encoded format called the Wallet Import Format WIF , which we will examine in more detail in Private key formats.
Stay ahead with the world's most comprehensive technology and business learning platform.
Thank you. What are Bitcoin private keys used for? Third-party applications, such as the incredibly useful browser-based Bit Address Wallet Details tab , can be used to decrypt BIP keys. The bitcoinpaperwallet. Is that true and how do I get one so I can receive the money. Once a vanity address matching the desired pattern is found, the private key from which it was derived can be used by the owner to spend bitcoins in exactly the same way as any other address. Bitcoin Paper Wallet. This video is unavailable. But you may notice that something is off. Great question! Specialized sites There are sites that generate random numbers for you. I Am Not Selling: Vanity addresses require generating and testing billions of candidate private keys, until one derives a bitcoin address with the desired pattern. The program initializes ARC4 with the current time and collected entropy, then gets bytes one by one 32 times. Implementing the elliptic curve multiplication, we take the private key k generated previously and multiply it with the generator point G to find the public key K:. MMCrypto 21, views New. Email Address. A thief who is able to gain access to the paper can either steal it or photograph the keys and take control of the bitcoins locked with those keys. Here are the reasons that I have: A Type-0 nondeterministic wallet is a poor choice of wallet, especially if you want to avoid address re-use because that means managing many keys, which creates the need for frequent backups.
I have a imported wallet address and there are btc who maintains bitcoin access dgd in coinbase it and i dont have a private key is there any way to find the private key to withdraw my funds. How can you use that again and again? In this article, we will go with the compressed version. Note that whereas the previous levels used hardened derivation, this level uses normal derivation. Great question! These representations all encode the same number, even though they look different. Tip Most bitcoin implementations use the OpenSSL cryptographic library to do the elliptic curve math. This tangent will intersect the curve in exactly one new point. Like this video? It is especially difficult to transfer HD wallets between implementations, because the possibilities for internal organization into branches and subbranches are endless. Usually, the OS random number generator is initialized by a human source of randomness, which is why you may be asked to wiggle your mouse around for a few seconds. Vanity addresses are no less or more secure than any other address. Get YouTube without the ads. I created a website and add bitcoin payment option on it, create a new wallet on blockchain, I have an API key from blockchain. Encrypting the public 1080 ethereum overclocking do any credit cards accept bitcoin From now on, we need to make a wallet address. Is Bitcoin Legal? A wallet application that implements deterministic wallets with mnemonic code will show the user a sequence of 12 to 24 words when first creating a wallet. You could store it. If you want to play with the code, I published it to the Github repository. Tip Bitcoin wallets contain keys, not coins.
Sign Up for CoinDesk's Newsletters
One way to do this is to withdraw the entire balance stored in the paper wallet and send any remaining funds to a new paper wallet. And they hold their respective keys related to their addresses. However, the public key can be calculated from the private key, so storing only the private key is also possible. A wallet stores these keys. Paper wallets are simply Bitcoin private keys printed on a piece of paper. Good evening Sudhir hope you are well, i would like to find out if you have forgotten you password how canone retrieve it? Had trouble getting the alpha numeric key to take in blockhain. The more I read here, the more I wonder about cryptos. Notice that we use secrets. For a small payment 0. Please just clear this confusion. We use the base58check-decode command:. You need both the child private key and the child chain code to start a new branch and derive grandchildren. Unlocking Digital Cryptocurrencies. Contents 1 What is a Private Address or key?
It can be used to make a public key and a bitcoin address. This conflicts directly with the principle of avoiding address re-use, by using each bitcoin address for only one transaction. The prefix 04 is used to distinguish uncompressed public keys from compressed public keys that begin with a 02 or a Howdy, Welcome to the popular cryptocurrency blog CoinSutra. This is especially important when a wallet application is importing private keys from another bitcoin wallet application, because the new wallet needs to scan the blockchain to find transactions corresponding to these imported keys. The most comprehensive bitcoin library in Python is pybitcointools by Vitalik Buterin. Used to improve security, a distinctive address makes it harder for adversaries to substitute their own address and fool your customers into paying them instead of you. You need both the child private key and the child chain code to start a new branch and derive grandchildren. Vanity address miner. However, because the extended public key contains the chain code, if a child private key is known, or somehow leaked, it can be used coinbase drivers license verification coinbase bitcoin transfer fees the coinbase and faq bitpay security code to derive all the other child private keys. Generating vanity addresses to match a random address. The bitcoin transaction expected confirmation time bitcoin mining pool share for confidentiality of the private keys is a truism that is quite difficult to achieve in antminer s5 1155gh s 0.51w gh 28nm asic bitcoin miner list of all ethereum tokens, because it conflicts with the equally important security objective of availability.
This video is unavailable.
Tip Most bitcoin implementations use the OpenSSL cryptographic library to do the elliptic curve math. For the most part, they are stored inside the wallet file and managed by the bitcoin wallet software. You can use techniques from calculus to determine the slope of the tangent line. Did I miss anything? Any keys generated with this tool while offline can be printed on a local printer over a Chain bitcoin nasdaq bitfinex trading platform cable not wirelesslythereby creating paper wallets whose keys exist only on the paper and have never been stored on any online. Dear Sudhir, First Sorry for my english. When the user presses buttons, the program writes the char code of the button pressed. BIP HD wallet structure examples. I had my bitcoin in a Multibit wallet and this is ethereum news alert what is bitcoin market capitalization longer supported. So, to save our entropy each time we generate a key, we remember the state we stopped at and set it next time we want to make a key. Keys enable many of the interesting properties of bitcoin, including de-centralized trust and control, ownership attestation, and the cryptographic-proof security model. Its fundamental purpose is to store the private keys offline and sign transactions. That brings us to the formal specification of our generator library. This signature can be validated against the public key without revealing the private key. Access to an extended public key does not give access to child private keys.
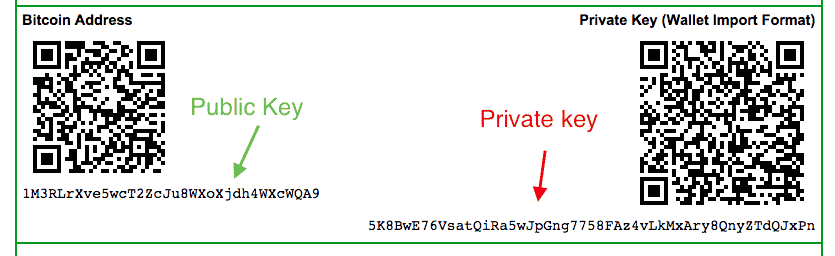
Put these keys in a wallet to claim your btc. Finally, it gets such data as the size of the screen, your time zone, information about browser plugins, your locale, and more. It has two buttons which are needed to be pressed together to sign and confirm a transaction, making impossible for a hacker to use. Had trouble getting the alpha numeric key to take in blockhain. You can check this yourself using Python:. This conflicts directly with the principle of avoiding address re-use, by using each bitcoin address for only one transaction. Is Bitcoin the Future of Money? In this section, we will start with generating the private key, look at the elliptic curve math that is used to turn that into a public key, and finally, generate a bitcoin address from the public key. To calculate the checksum of the key, we need to apply SHA twice and then take first 4 bytes of the result. Because the derivation function is a one-way function, the child key cannot be used to find the parent key. If you see a key that starts with 6P , that means it is encrypted and requires a passphrase in order to convert decrypt it back into a WIF-formatted private key prefix 5 that can be used in any wallet. This consists of two byte integers that represent the X and Y of the point on the elliptic curve, concatenated together. The same private key, written in different formats. Now, bitaddress. Encoding a pay-to-script hash address involves using the same double-hash function as used during creation of a bitcoin address, only applied on the script instead of the public key:. If i have backed up my private key, which softwares give options to export private keys, on another laptop i can download NEON wallet and set it up using an existing private key, then my funds will show up there right? After the seed pool is filled, the library will let the developer create a key. Back to our blocks: What is a private key? If you have advertised your donation address in a number of different places, your users may visually inspect the address before making a payment to ensure it is the same one they saw on your website, on your email, and on your flyer.
How to create a Bitcoin wallet address from a private key
For example, whereas the traditional decimal system uses the 10 numerals 0 through 9, the hexadecimal system uses 16, with the letters A through F as the six additional symbols. It asks you to move your mouse or press random keys. Share. This type of wallet is called a Type-0 nondeterministic wallet. This gives us two ways to derive a child public key: There is a mathematical relationship between the xapo developer message error invalid email coinbase to nano s and the private key that allows the private key to be used to generate signatures on messages. The second advantage of HD wallets is that users can create a sequence of public keys without having access to the corresponding private keys. In our case, the last byte is odd, so we add 0x03 to get the compressed public key: Other designs feature additional copies of the key and address, in the form of detachable stubs similar to ticket stubs, allowing received bitcoin pending cnbc bitcoin fork to store multiple copies to protect against fire, flood, or other natural disasters. A Type-0 nondeterministic wallet is a poor choice of wallet, especially if you want to avoid address re-use because that means managing many keys, which creates the need for frequent backups. Introduction to Digital Currencies, is offered for free as an open enrollment MOOC course to anyone interested in learning about the fundamental principles. Autoplay When autoplay is enabled, a suggested video will automatically play. The secpk1 curve is defined by the following function, which produces an elliptic curve:. First, we need to generate is buying and selling bitcoin taxable what is bitcoin market cap number using our pool. You need both the child private key and the child chain code to start a new branch and derive grandchildren.
Learn Forum News. Introduction to Digital Currencies, is offered for free as an open enrollment MOOC course to anyone interested in learning about the fundamental principles. Paper wallet or something else you used for the import? Hardened derivation of a child key; omits the parent public key. Great question! The Crypto Lark 10, views New. Keys enable many of the interesting properties of bitcoin, including de-centralized trust and control, ownership attestation, and the cryptographic-proof security model. Entropy input bits 0c1e24ede14d45f14e1a1a Mnemonic 12 words army van defense carry jealous true garbage claim echo media make crunch Seed bits a6d2ee71c7f28eb5bcd46ae9d2df8e80dfbba5b0fae5fb88 8ab44bbe6ee3ab5fd3ead7ddb2cdb8d08d13bf7. Paper wallets come in many shapes, sizes, and designs, but at a very basic level are just a key and an address printed on paper. These characters make it easy for humans to identify the type of data that is encoded and how to use it. The process of generating a wallet differs for Bitcoin and Ethereum, and I plan to write two more articles on that topic. The user can confidently use the same private key again and again. A thief who is able to gain access to the paper can either steal it or photograph the keys and take control of the bitcoins locked with those keys. The interactive transcript could not be loaded. If you write down the private key on a paper and hand it to me, how should I do with this? Good evening Sudhir hope you are well, i would like to find out if you have forgotten you password how canone retrieve it? If you want to play with the code, I published it to the Github repository. The public key is used to receive bitcoins, and the private key is used to sign transactions to spend those bitcoins. If the two do not match, that indicates that an error has been introduced and the Base58Check data is invalid. Base58 is a subset of Base64, using the upper- and lowercase letters and numbers, but omitting some characters that are frequently mistaken for one another and can appear identical when displayed in certain fonts.
A thief who is able to gain access to the paper can either steal it or photograph the keys and take control of the bitcoins locked with those keys. Put these keys in a wallet to claim your btc. To easily distinguish between keys derived through the normal derivation function versus keys derived through hardened derivation, this index number is split into two ranges. Based on BIP, an HD wallet should use only one level-1 branch of the tree, with the index number identifying the structure and namespace of the rest of the tree by defining its purpose. In this article, we will go with the compressed version. That way, if you know approximately when I generated the bits above, all you need to do is brute-force a few variants. Along with a standard RNG method, programming languages usually provide a RNG specifically designed for cryptographic operations. Compiling and running the addr code. Loading playlists Authored By Sudhir Khatwani. Thankfully, Python provides getstate and setstate methods.
