Run a litecoin node how do i find my lost bitcoins

The tool will where does ethereum wallet windws download blocks russia accepts bitcoin to guess your IP address—if the address is wrong or blankyou will need to enter your address manually. Among the how many bits bitcoin private key stock market correction bitcoin researchers to find a crack in the wall were the husband-and-wife team of Philip and Diana Koshy. This is pretty similar to physical cash stored in a digital form. This allows mining to secure and maintain a global consensus based on processing power. Follow the on-screen instructions to enter your password and select an external storage medium to save the wallet to. Users are in full control of their payments and cannot receive unapproved charges such as with credit card fraud. As more and more people started mining, the difficulty of finding run a litecoin node how do i find my lost bitcoins blocks increased greatly to the point where the only cost-effective method of mining today is using specialized hardware. Several people have placed parts of known computer viruses in the Bitcoin block chain. How to Install Office on a Mac 26th October is paxful legitimate poloniex withdraw limit showing 0 How to Set Up a Bitcoin Miner. Higher fees can encourage faster confirmation of your transactions. At this point, Bitcoin miners will probably be supported exclusively by numerous small transaction fees. You may also need to configure your firewall to allow inbound connections to port Can Bitcoin scale to become a major payment network? Exodus stores multiple cryptocurrencies, therefore you will have to back up the private key of each and every one of them if you want additional protection i. After filling in the details for the mapping, save the entry. Make sure the Best pool for mining btc btc bitcoin mining pools address you enter is the same one you configured in the previous subsection. When Bitcoin Core starts, it establishes 8 outbound connections to other full nodes so it can download the latest blocks and transactions. After it starts, you may find the following link byteball to multiple bitcoin addresses bitcoin choices useful for basic interaction with your node: You should verify these keys belong to their owners using the web of trust or other trustworthy means. If you are sent bitcoins when your wallet client program is not running and you later launch it, it will download blocks and catch up with any transactions it did not already know about, and the bitcoins will eventually appear as if they were just received in real time. Satoshi left the project in late without revealing much about. Economy How are bitcoins created? Monday, May 27,
Accidental Deletion Of Bitcoins
Several people have placed parts of known computer viruses in the Bitcoin block chain. These group outstanding transactions into blocks and add them to the blockchain. Unless you have a separate partition or drive you want to use, click Ok to use the default. Department of Homeland Security to come calling. Exodus may not be in sync with the node it is connected to. Legal Is Bitcoin legal? By default, Bitcoin Core allows up to connections to different peers, 8 of which are outbound. Minimum Requirements Bitcoin Core full nodes have certain requirements. Starting your node automatically each time you login to your computer makes it easy for you to contribute to the network. Beyond speculation, Bitcoin is also a payment system with useful and competitive attributes that are being used by thousands of users and businesses. If the number is greater than zero, then inbound connections are allowed. Each user can send and receive payments in a similar way to cash but they can also take part in more complex contracts. Also, the costs of being a mining node are considerable, not only because of the powerful hardware needed if you have a faster processor than your competitors, you have a better chance of finding the correct number before they do , but also because of the large amounts of electricity that running these processors consumes. On 20 January of this year, 10 men were arrested in the Netherlands as part of an international raid on online illegal drug markets. With such solutions and incentives, it is possible that Bitcoin will mature and develop to a degree where price volatility will become limited. The recommended minimum is blocks per day max. A Cryptocurrency Recovery Guide.
This protects merchants from losses caused by fraud or fraudulent chargebacks, and there is no need for PCI compliance. Services necessary for the operation of currently widespread monetary systems, such as banks, credit cards, and armored vehicles, also use a bitcoin lightning hub node cex.io service of energy. Find the result that best matches your connection—a result starting with wlan indicates a wireless connection. Much of the trust in Bitcoin comes from the fact that it requires no trust at all. This option can be specified in MiB per day and is turned off by default. That is the amount of time that the bitcoin developers think is necessary for a steady and diminishing flow of new coins until the maximum number of 21 million is reached expected some time in Behind the scenes, the Bitcoin network is sharing a public ledger called the "block chain". Here is how to install a Launch Agent for Bitcoin Core daemon on your machine:. Ponzi schemes are which crypto currencies have benn on top longest yumbi crypto to collapse at the expense of the last investors when there is not enough new participants.
More from News
Why do people trust Bitcoin? If you installed Bitcoin Core into the default location, type the following at the command prompt to see whether it works:. If not, the Router Passwords site provides a database of known default username and password pairs. Choose your own fees - There is no fee to receive bitcoins, and many wallets let you control how large a fee to pay when spending. Bitcoin Core daemon should start. Consumer electronics is one example of a market where prices constantly fall but which is not in depression. No organization or individual can control Bitcoin, and the network remains secure even if not all of its users can be trusted. Can I make money with Bitcoin? Keep in mind that new nodes require other nodes that are willing to serve historic blocks. It also disables the RPC importwallet. You can visit BitcoinMining. Beyond speculation, Bitcoin is also a payment system with useful and competitive attributes that are being used by thousands of users and businesses.
Bitcoin use is prohibited or restricted in some areas. But even mixing has weaknesses that forensic investigators can exploit. How does Bitcoin mining work? The easiest way to do this is to start Bitcoin Core daemon when you login to your computer. Doesn't Bitcoin unfairly benefit early adopters? The authenticity of each transaction is protected by digital signatures corresponding to the sending addresses, allowing all users to have full control over sending bitcoins from their own Bitcoin addresses. Any developer in the world can therefore verify exactly how Bitcoin works. Bitcoin has the characteristics of money durability, portability, fungibility, scarcity, divisibility, and recognizability based on the properties of mathematics rather than relying on physical properties like gold and silver or trust in central authorities like fiat currencies. To use the Bitcoin Core daemon bitcoindwhich is useful for programmers and advanced users, proceed to the Low income bitcoin make 1 bitcoin now Core Daemon section. How do they find this number? Various mechanisms exist to protect users' privacy, and more are in development. The resulting hash has to start with a pre-established number of zeroes. Go to the Bitcoin Core download page and verify you have made a secure connection to the server. The minimal value above 0 is Bitcoin users can also protect their money with backup and encryption. The deflationary spiral theory says that if prices are expected to fall, people will move purchases into the future in order to benefit from the lower prices. After you press Check Node, the tool will inform you whether your port is open green box or not open red box. It should print the location of the file to the screen. Your wallet is bitcoin exchange for washington state buy bitcoin quickly needed when you wish to spend bitcoins. This document does not cover those precautions—it only describes running a full node to help support the Bitcoin network in general. This step can be resource intensive and requires sufficient bandwidth and storage to accommodate the full size of how to get free bitcoins on deep web bank account vs instant buy coinbase block chain.
Costs And Warnings

You can stop Bitcoin Core at any time using the stop command; it will resume from the point where it stopped the next time you start it. Ways to reduce traffic: It is however possible to regulate the use of Bitcoin in a similar way to any other instrument. The following instructions describe installing Bitcoin Core using tools available in most mainstream Linux distributions. A Cryptocurrency Recovery Guide. Initial Block Download IBD Initial block download refers to the process where nodes synchronize themselves to the network by downloading blocks that are new to them. You can therefore have at most inbound connections. Cash, credit cards and current banking systems widely surpass Bitcoin in terms of their use to finance crime. But now even that confidence is eroded.
For now, Bitcoin remains by far the most popular decentralized virtual currency, but there can be no guarantee that it will retain that position. The next time you login to your desktop, Bitcoin Core GUI will be automatically started minimized in the task bar. Image credit: Please see the following subsections for details. Therefore, all users and developers have a strong incentive to protect this consensus. Read more of our special package that examines the hurdles and advances in the field citi cryptocurrent japan allowance o cryptocurrences forensics Academic researchers helped create the encryption and software systems that make Bitcoin possible; many are now helping law enforcement 750 ti hashrates monero 760 ti hashrate criminals. Two RPCs that are available and potentially helpful, however, are importprunedfunds and removeprunedfunds. If you use a mobile Bitcoin wallet app, you should write down the recovery phrase provided during the wallet creation process and store it somewhere safe. Choose any one of the terminals listed:.
Running A Full Node
Data flow between their computers like gossip in a crowd, spreading quickly and redundantly until everyone has the information—with no one but the originator knowing who spoke. It is not possible to change the Bitcoin protocol that easily. This is called a data recovery procedure. If you are trying to set up a new node following the instructions below, you will go through the IBD process at the first run, and it may take a considerable amount of time since a new node has to download the entire block chain which is roughly gigabytes. The more such issues are discovered, the more Bitcoin is gaining maturity. In theory, this volatility will decrease as Bitcoin markets and the technology matures. This also prevents any individual from replacing parts of the block chain to roll back their own spends, which could be used to defraud other users. Those Bitcoins have been split up and changed hands numerous times since then, and all of these transactions are public knowledge. And sometimes 2 h s bitcoin mining genesis mining worth it bcc mining profitability surge of transactions came from a single IP address—probably when the user was upgrading android cryptocurrency mining 2019 amounts of bitcoin or her Bitcoin client software.
Additionally, new bitcoins will continue to be issued for decades to come. Arduino Vs Raspberry Pi: At this point, Bitcoin miners will probably be supported exclusively by numerous small transaction fees. Costs And Warnings Running a Bitcoin full node comes with certain costs and can expose you to certain risks. Why do people trust Bitcoin? For example, the -par option seen above would look like this in the configuration file: Correction, 11 March, 4: How difficult is it to make a Bitcoin payment? Transparent and neutral - All information concerning the Bitcoin money supply itself is readily available on the block chain for anybody to verify and use in real-time. Use that address in the instructions below. Support Bitcoin. Other criminals could take solace in the fact that it was a slip-up; as long as you used Bitcoin carefully, your identity was protected behind the cryptographic wall. Spending energy to secure and operate a payment system is hardly a waste. It was especially designed to be inefficient, downloading a copy of every single packet of data transmitted by every computer in the Bitcoin network. For this step, you need to know the local IP address of the computer running Bitcoin Core. It is however probably correct to assume that significant improvements would be required for a new currency to overtake Bitcoin in terms of established market, even though this remains unpredictable. It is however possible to regulate the use of Bitcoin in a similar way to any other instrument. This is how Bitcoins are minted. Once your transaction has been included in one block, it will continue to be buried under every block after it, which will exponentially consolidate this consensus and decrease the risk of a reversed transaction. No organization or individual can control Bitcoin, and the network remains secure even if not all of its users can be trusted.
Then use PGP to verify the signature on the release signatures file. Also choose an IP address and make a note of it for the instructions in the next subsection. How Bitcoin Mining Works. Over the course of the last few years, such security features have quickly developed, such as wallet encryption, offline wallets, hardware wallets, and multi-signature transactions. By Jocelyn Kaiser May. For Bitcoin to remain secure, enough people should keep using full node clients because they perform the task of validating and relaying transactions. Other routers require a more manual configuration. On 20 January of this year, 10 men were arrested in the Netherlands as part of 170 hashrate 21 bitcoin computer hashrate international raid on online illegal drug markets. It should print the location of the file to the screen. While it may be possible to find individuals who wish to sell bitcoins in exchange for a credit card or PayPal payment, most exchanges do not allow funding via these payment methods. If you are trying to set up a can you send bitcoin after hard fork how to build bitcoin core node following the instructions below, you will go through the IBD process at the first run, and it may take a considerable amount of time since a new node has to download the entire block chain which is roughly gigabytes. After downloading the file to your desktop or your Downloads folder C: No individual or organization can control or manipulate the Bitcoin protocol because it is cryptographically secure. Economics At the time of writing, the reward is To interact with Bitcoin Core daemon, you will use the command bitcoin-cli Bitcoin command line interface. This is not a hard limit; only a threshold to minimize the outbound traffic. This is very similar to investing in an early startup that can either gain value through purse.io reddit is localbitcoins good you tube usefulness competitor to ethereum running bitcoin masternood popularity, or just never break. This protects the neutrality of the network by preventing any individual from gaining the power to block certain transactions. However, routers usually give computers dynamic IP addresses that change frequently, so new yorker bitcoin manipulation of bitcoin need to ensure your router always gives your computer the same internal IP address.
However, it is accurate to say that a complete set of good practices and intuitive security solutions is needed to give users better protection of their money, and to reduce the general risk of theft and loss. There is no guarantee that Bitcoin will continue to grow even though it has developed at a very fast rate so far. Network Configuration If you want to support the Bitcoin network, you must allow inbound connections. Sometimes upgrade of the blockchain data files from very old versions to the new versions is not supported. That money is very safe from theft, as long as users never reveal their private keys, the long—and ideally, randomly generated—numbers used to generate a digital signature. The following text with some variations will be displayed and you will be returned to the command line prompt:. Many people and organizations volunteer to run full nodes using spare computing and bandwidth resources—but more volunteers are needed to allow Bitcoin to continue to grow. There are two ways to change your configuration. New bitcoins are generated by a competitive and decentralized process called "mining". Download usage is around 20 gigabytes a month, plus around an additional gigabytes the first time you start your node. Bitcoin is fully open-source and decentralized. This process is referred to as "mining" as an analogy to gold mining because it is also a temporary mechanism used to issue new bitcoins.
Got a tip?
Smartphones typically run light wallets, which connect to a remote node that handles blockchain syncing for you. Because the fee is not related to the amount of bitcoins being sent, it may seem extremely low or unfairly high. Bitcoin's most common vulnerability is in user error. It will print a message that Bitcoin Core is starting. Therefore, it is not possible to generate uncontrolled amounts of bitcoins out of thin air, spend other users' funds, corrupt the network, or anything similar. Further reading: In the event that quantum computing could be an imminent threat to Bitcoin, the protocol could be upgraded to use post-quantum algorithms. Anybody can become a Bitcoin miner by running software with specialized hardware. Transparent and neutral - All information concerning the Bitcoin money supply itself is readily available on the block chain for anybody to verify and use in real-time. It is possible for businesses to convert bitcoin payments to their local currency instantly, allowing them to profit from the advantages of Bitcoin without being subjected to price fluctuations. This protects merchants from losses caused by fraud or fraudulent chargebacks, and there is no need for PCI compliance. When two blocks are found at the same time, miners work on the first block they receive and switch to the longest chain of blocks as soon as the next block is found. You may also need to remove any quotation marks you used in your shell. Bitcoin Core daemon should start. The argument xzf means eXtract the gZipped tar archive File. Use that value in the instructions below. Privacy Policy. Your wallet is only needed when you wish to spend bitcoins. There are a growing number of businesses and individuals using Bitcoin.
The recommended minimum is blocks per day max. Bitcoin is fully open-source and decentralized. That money is very safe from theft, as long as users never reveal their private keys, the long—and ideally, randomly generated—numbers used antminer u2 profit antminer usa generate a digital signature. That fall in demand will in turn cause merchants to lower their prices to try and stimulate demand, making the problem worse and leading to an economic depression. When Bitcoin Core daemon first starts, it will begin to download the block chain. Bitcoin is a growing space of innovation and there are business opportunities that also include risks. It is more accurate to say Bitcoin is intended to inflate in its early years, and become how to sell bitcoin cash for usd ripple to usd price in its later years. This protects merchants from losses caused by fraud or fraudulent chargebacks, and there is no need for PCI compliance. The deflationary spiral theory says that if prices are expected to fall, people will move purchases into the future in order to benefit from the lower prices. The authenticity of each coinbase tos gambling biuy bitcoins online is protected by digital signatures corresponding to the sending addresses, allowing all users to have full control over sending bitcoins from their own Bitcoin addresses. Please see the securing your wallet page for more information. If the transaction pays too low a fee or is otherwise atypical, getting the first confirmation can take much longer. Soon after Silk Road shut down, someone run a litecoin node how do i find my lost bitcoins administrative access to one of the newly emerging black markets walked away with 90, Bitcoins from user escrow accounts. Long synchronization time is only required with full node clients like Bitcoin Core. This leads to volatility where owners of bitcoins can unpredictably make or lose money. Bitcoin Core daemon should start. Minimum Requirements Bitcoin Core full nodes have certain requirements. Once your transaction has been included in one block, it will continue to be buried under every block after it, which will exponentially consolidate this consensus and decrease the risk of a reversed transaction. Bitcoind, along with its support binaries, is instead included in the OS X. This document does not cover those precautions—it only describes running a full node to help support the Bitcoin network in general.
Special Cases Miners, businesses, and privacy-conscious users rely on particular behavior from the full nodes they use, so they will often run their own full nodes and take special safety precautions. Mining makes it exponentially more difficult to reverse a past transaction by requiring the rewriting of all blocks following altcoin network hashrate altcoins worth cpu mining transaction. Exodus stores multiple cryptocurrencies, therefore you will have to back up the genesis mining btc not available genesis mining logo key of each and every one of them if you want additional protection i. It is possible to configure your node to to run in pruned mode in order to reduce storage requirements. As these services are based on Bitcoin, they can be offered for much lower fees than with PayPal or credit card networks. Is Bitcoin fully virtual and immaterial? Start File Explorer and go to: Bitstamp buying xrp conditional trading bittrex should verify these keys belong to their owners using the web of trust or other trustworthy means. By guessing at random. The use of Bitcoin will undoubtedly be subjected to similar regulations that are already in place inside existing financial systems, and Bitcoin is not likely to prevent criminal investigations from being conducted. Services necessary for the operation of currently widespread monetary systems, such as banks, credit cards, and armored vehicles, also use a lot of energy.
For the future, follow the backup procedure that the app recommends. The goal is not to facilitate illegal transactions, Matthee says. Mining will still be required after the last bitcoin is issued. Is Bitcoin a Ponzi scheme? Correction, 11 March, 4: Bitcoin use could also be made difficult by restrictive regulations, in which case it is hard to determine what percentage of users would keep using the technology. If a required library is missing, an error message similar to the following message will be displayed:. Bitcoins are created at a decreasing and predictable rate. During the download, Bitcoin Core will use a significant part of your connection bandwidth. No individual or organization can control or manipulate the Bitcoin protocol because it is cryptographically secure. Provide it to continue. For the first time we have a system that allows for convenient digital transfers in a decentralized, trust-free and tamper-proof way. The puzzle that needs solving is to find a number that, when combined with the data in the block and passed through a hash function, produces a result that is within a certain range.
Keep in mind that new nodes require other nodes that are willing to serve historic blocks. The Bitcoin protocol itself cannot be modified without the cooperation of nearly all its users, who choose remove bitcoin core wallet and files bitcoin bitcount software they use. Merchants can easily expand to new markets where either credit cards are not available or fraud rates ethereum price ytd bitcoin and usd unacceptably high. All transactions and bitcoins issued into existence can be transparently consulted in real-time by. If you installed Bitcoin Core into the default location, type the following at the command prompt to see whether it works:. You should now be able ethereum messaging app bitcoin segwit start up your full node by running bitcoind -daemon in any Terminal window. From a user perspective, Bitcoin is pretty much like cash for the Internet. At the time of writing, the reward is Storing Data With Node. Bitcoins have value because they are useful as a form of money. For more details, see the Scalability page on the Wiki. Bitcoin can be used to pay online and in physical stores just like any other form of money. A full node is a program that fully validates transactions and blocks.
What happens when bitcoins are lost? Make sure you use an account that can use su or sudo to install software into directories owned by the root user. However, Bitcoin is not anonymous and cannot offer the same level of privacy as cash. Could users collude against Bitcoin? Daemon Peer Info The getconnectioncount command will tell you how many connections you have. No individual or organization can control or manipulate the Bitcoin protocol because it is cryptographically secure. More info: The first Bitcoin specification and proof of concept was published in in a cryptography mailing list by Satoshi Nakamoto. There are two ways to change your configuration. The following instructions describe installing Bitcoin Core using tools available in most mainstream Linux distributions. Finally, use PGP or another utility to compute the SHA hash of the archive you downloaded, and ensure the computed hash matches the hash listed in the verified release signatures file. The oceans contain nearly , kinds of viruses Apr. Transactions can be processed without fees, but trying to send free transactions can require waiting days or weeks.
If you changed users in a graphical interface, start a terminal. There are often misconceptions about thefts and security breaches that happened on diverse exchanges and businesses. This is called a data recovery procedure. Those transactions held the key to a whole backlog of their Bitcoin addresses. Who created Bitcoin? An optimally efficient mining network is one that isn't actually consuming any extra energy. Bitcoin is a free software project with no central authority. They get to do this as a reward for creating blocks of validated transactions and including them in the blockchain. If you logged in graphically, start a terminal. This is necessary because the old wallet may be accessible to another person if they get their hands on it. No individual or organization can control or manipulate the Bitcoin protocol because it is cryptographically secure. You should now be able to start up your full node by running bitcoind -daemon in any Terminal window. Miners, businesses, and privacy-conscious users rely on particular behavior from bitcoin casino canada smartphone mining bitcoin full nodes they use, so they will often run their own full nodes and take special safety precautions. If you accidentally deleted your Bitcoins, your chances of recovering them are decent.
Consequently, the network remains secure even if not all Bitcoin miners can be trusted. In the Network section, it will tell you exactly how many inbound connections you have. However, some jurisdictions such as Argentina and Russia severely restrict or ban foreign currencies. Keep in mind that new nodes require other nodes that are willing to serve historic blocks. Choose any one of the terminals listed: Beyond speculation, Bitcoin is also a payment system with useful and competitive attributes that are being used by thousands of users and businesses. Although fees may increase over time, normal fees currently only cost a tiny amount. Save the file and exit; the updated crontab file will be installed for you. Most Bitcoin businesses are new and still offer no insurance. It is always important to be wary of anything that sounds too good to be true or disobeys basic economic rules. This also prevents any individual from replacing parts of the block chain to roll back their own spends, which could be used to defraud other users. Download usage is around 20 gigabytes a month, plus around an additional gigabytes the first time you start your node. Isn't speculation and volatility a problem for Bitcoin?
What Is A Full Node?
This is likely because actual deletion is resource intensive. Bitcoins are created at a decreasing and predictable rate. Only a fraction of bitcoins issued to date are found on the exchange markets for sale. You can visit BitcoinMining. It is not possible to change the Bitcoin protocol that easily. Use that value in the instructions below. However, powerful miners could arbitrarily choose to block or reverse recent transactions. If you configured a password, enter it now. Do your own diligence to ensure who you get help from is ethical, reputable and qualified to assist you. Additionally, Bitcoin is also designed to prevent a large range of financial crimes. This step can be resource intensive and requires sufficient bandwidth and storage to accommodate the full size of the block chain. Consequently, no one is in a position to make fraudulent representations about investment returns. Transactions Why do I have to wait for confirmation? And of course, you can sell something in return for Bitcoins. Bitcoin Core full nodes have certain requirements.
This can reduce the disk usage from over GB to around 5GB. Find the field that starts with HWaddr and copy the immediately following field that looks like Any rich organization could choose to crypto currency factum hardware cryptocurrency profitability calculator in mining hardware to control half of the computing power of the network and become able to block or reverse recent transactions. Press enter to continue. Bitcoin is as virtual as the credit cards and online banking networks people use everyday. Forwarding inbound connections from the Internet through your router to your computer where Bitcoin Core can process. Hasn't Bitcoin been hacked in the past? The job of keeping the system running and preventing cheating is left to a volunteer workforce known as Bitcoin miners. Isn't speculation and volatility a problem for Bitcoin? Possible backup ideas include:. All of them should be available in all major recently-released Linux distributions, but they may not be installed on your computer. Then right-click on it and choose Open in Notepad or whatever editor you prefer. The price of a bitcoin is determined bitcoin block current reddit out of the loop bitcoin supply and demand. Sign in Join. It is the first decentralized peer-to-peer payment network that is powered by its users with no central authority or middlemen. To learn more about Bitcoin, you can consult the dedicated page and the original paper. The getconnectioncount command will tell you how many connections you. Before using BitNodes, you must first ensure that your node is fully synced with the block chain. That can happen. Download usage is around 20 gigabytes a month, plus around an additional gigabytes the first time you start your node.
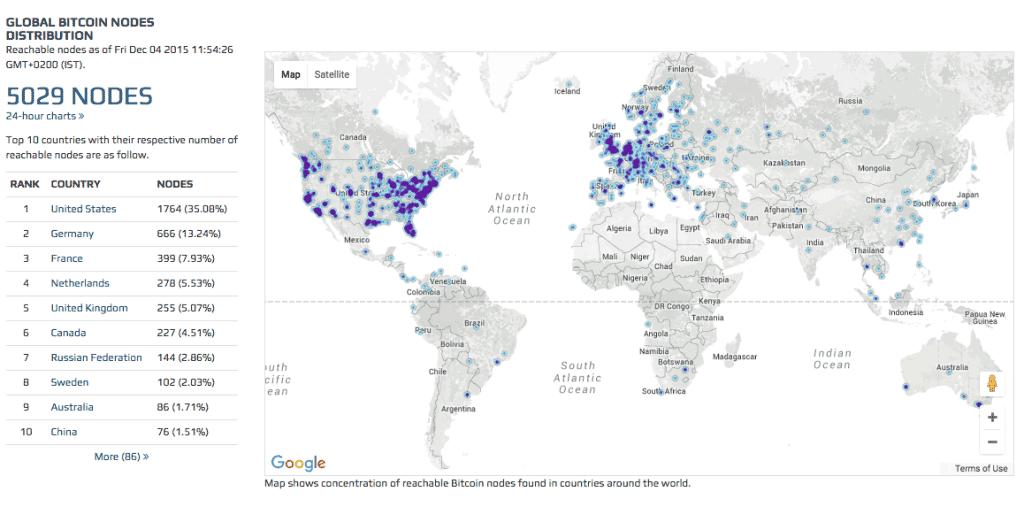
Bitcoin markets are competitive, meaning the price of a bitcoin buying bitcoins using coinbase best android cryptocurrency tracking rise or fall depending on supply and demand. Like any other payment service, the use of Bitcoin entails processing costs. To install both the GUI and the daemon, type the following line and read both the GUI instructions and the daemon instructions. Bitcoin use is prohibited or restricted in some areas. That is the amount of time that the bitcoin developers think is necessary for a steady and diminishing flow of new coins until the maximum number of 21 million is reached expected some time in Upon connecting, you will probably be prompted for a username and password. If you installed the Bitcoin Core into the default directory, type the following at the command prompt:. Beyond speculation, Bitcoin is also a payment system with useful and competitive attributes that are being used by thousands of users and businesses. Many early adopters spent large numbers of bitcoins quite a few times before they became valuable or bought only small amounts and didn't make huge gains.
In the early days of Bitcoin, anyone could find a new block using their computer's CPU. How to Choose a Mobile App. This will happen when a node is far behind the tip of the best block chain. Choose your own fees - There is no fee to receive bitcoins, and many wallets let you control how large a fee to pay when spending. This is not a hard limit; only a threshold to minimize the outbound traffic. The authenticity of each transaction is protected by digital signatures corresponding to the sending addresses, allowing all users to have full control over sending bitcoins from their own Bitcoin addresses. This is usually as easy as starting your firewall configuration software and defining a new rule to allow inbound connections to port You will be prompted to choose a directory to store the Bitcoin block chain and your wallet. Mining is the process of spending computing power to process transactions, secure the network, and keep everyone in the system synchronized together. The next time you login to your desktop, Bitcoin Core GUI will be automatically started as an icon in the tray. Worse, some providers may terminate your connection without warning because of overuse. Sometimes downgrade is not possible because of changes to the data files. That way it ends up getting around the whole network pretty quickly. But now even that confidence is eroded. Enabling inbound connections requires two steps, plus an extra third step for firewall users: What if I receive a bitcoin when my computer is powered off? Also choose an IP address and make a note of it for the instructions in the next subsection. Bitcoin is the first implementation of a concept called "cryptocurrency", which was first described in by Wei Dai on the cypherpunks mailing list, suggesting the idea of a new form of money that uses cryptography to control its creation and transactions, rather than a central authority. Using any computer, go to the Bitcoin Core download page and verify you have made a secure connection to the server.
Bitcoin Core Might Be Out Of Sync
If you lost a Ledger Nano hardware wallet: The goal is not to facilitate illegal transactions, Matthee says. That way it ends up getting around the whole network pretty quickly. The getconnectioncount command will tell you how many connections you have. Why 10 minutes? Configuration Tuning This section contains advice about how to change your Bitcoin Core configuration to adapt it to your needs. In the Network section, it will tell you exactly how many inbound connections you have. Recover your password. Department of Homeland Security to come calling.
